What is Next-Gen Vulnerability Management?
We develop Next-Gen Vulnerability Management to meet the modern and growing threat landscape. Compared to traditional vulnerability management, Next-Gen Vulnerability Management covers more attack vectors, includes ASM (Attack Surface Management) capabilities, and enriched threat intelligence - all in one unified platform - one unified view.
The four pillars of
Next-Gen Vulnerability Management
Attack vector coverage
Cover every corner of your IT infrastructure - including the users.
Attack Surface Management
Stay up to date with your attack surface and ensure it's fully covered.
Smart threat intelligence
Modern telemetry and AI enriching vulnerability data.
True unification
A truly unified platform with one risk model and one workflow to streamline prioritization and efficient mitigation.
This is how you benefit from Next-Gen
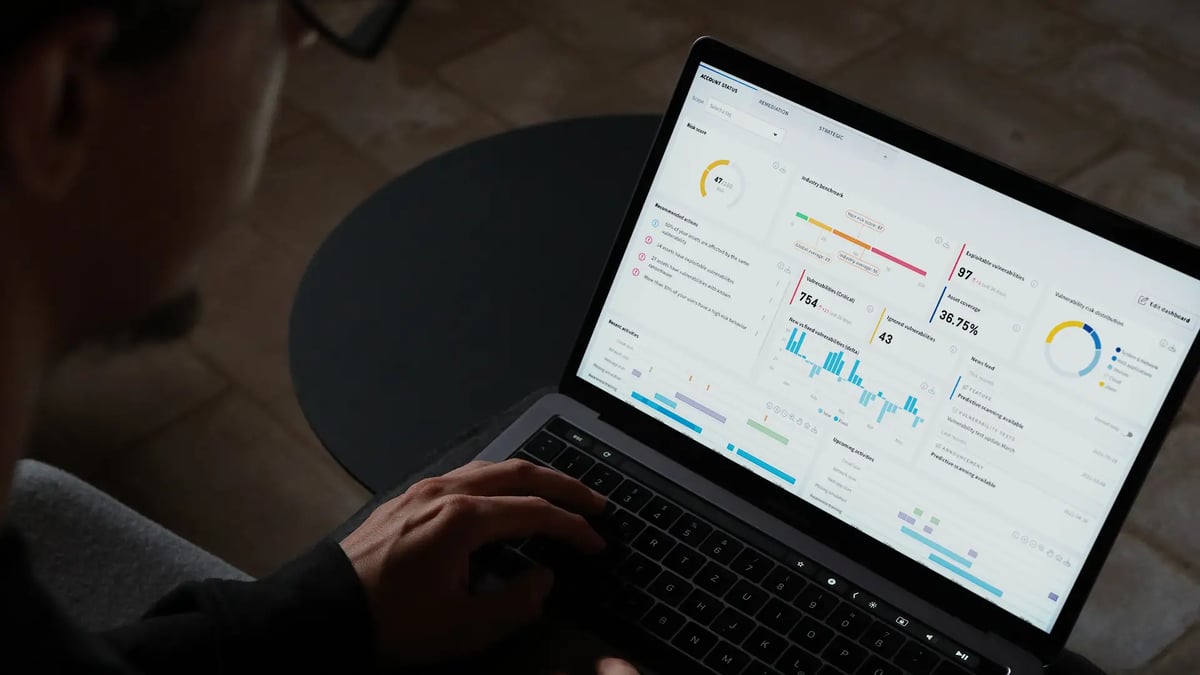

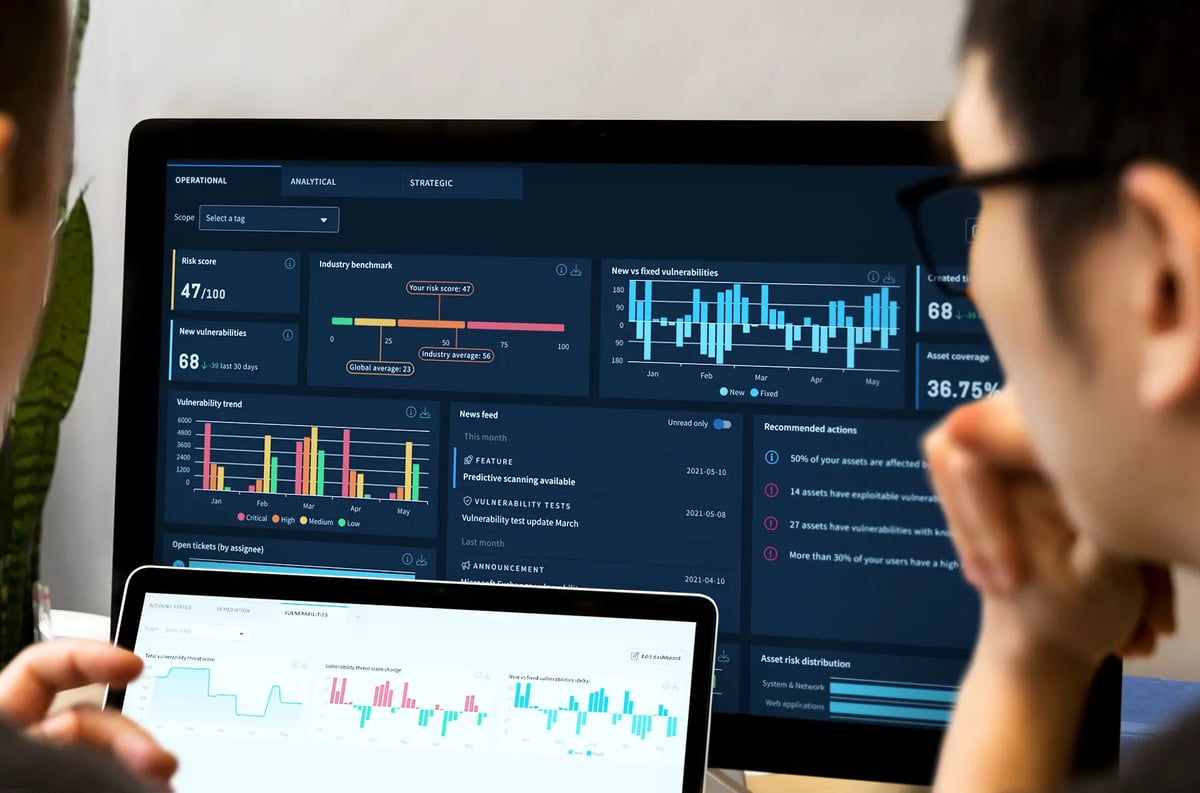

The key to measuring & improving organizational cyber security
The most crucial aspect of protecting your organization is the extent of the attack vector coverage for maintaining the security and integrity of systems, data, and users. The more attack vectors you cover, the more knowledge you will have to secure your business from risks.
Next-Gen Vulnerability Management extends attack vector coverage to cover your technical and human assets. We cover traditional systems, computers, cloud infrastructure and resources, web applications, APIs, IoT, OT/SCADA, and your human assets to ensure they are protected against phishing and ransomware.
Attack Surface Management – your shield against threats
Keeping up with the constantly changing attack surface has become a great challenge. The number of attack vectors and endpoints is not only growing but also changing over time.
The goal of ASM (Attack Surface Management) is to reduce the overall attack surface of an organization by identifying and eliminating blind spots and vulnerable systems. Attack Surface Management is built into our platform to identify and address potential security weaknesses before cybercriminals can exploit them.
Harness the power of smart threat intelligence
Just looking at the severity of a vulnerability is not enough to assess risk. The new threat landscape requires smarter threat intelligence.
Our method considers several key factors that contribute to the overall risk score associated with vulnerabilities. Closely monitor whether vulnerabilities are actively exploited, distinguishing between theoretical risks and those actively used by malicious actors. We assess the potential of vulnerabilities to be leveraged in ransomware attacks, enabling effective prioritization of mitigation efforts. Additionally, we evaluate whether vulnerabilities are exposed to the public-facing internet, which often requires urgent remediation. Our threat intelligence also provides insights into the number of assets that could be impacted, helping you allocate resources efficiently.
No more silos - streamline analysis, prioritization & remediation
Many organizations have built a big cyber security product stack over the years, which has become hard and inefficient to manage but also costly. On top of this, the products don’t interact in any way.
True unification is achieved by integrating all attack vectors into a unified platform with one risk model and one workflow. This enables a more streamlined work to mitigate risk and, simultaneously, helps you save both time and money.
Secure your IT infrastructure with Next-Gen Vulnerability Management!
Talk to a cyber security expert today
We’ll help you take steps to protect your business. Contact us to learn more.

The limitations of traditional vulnerability management
Traditional vulnerability management has been a cornerstone of a robust cyber security strategy for about 25 years. It enables organizations to identify and mitigate security risks proactively. However, traditional vulnerability management has limitations and doesn't meet the current threat landscape.
Limitations & weaknesses:
- Focuses on technical vulnerabilities in a limited number of attack vectors (systems and web applications) and overlooks human-centric attack vectors, including employees.
- Lack of context, or threat intelligence, to better understand and prioritize vulnerabilities.
- Requires considerable time and resources, making it a less-than-ideal solution for organizations with limited capabilities.
- Products that cover different attack vectors operate in silos without any integration.
- The lack of coordination among these tools leads to increased operational costs and diminished productivity.

Ready to enhance your cyber security with Next-Gen?
Book your consultation meeting today!
Frequently asked questions
What is Next-Gen Vulnerability Management?
Next-Gen Vulnerability Management is a development of traditional vulnerability management to meet the current and growing threat landscape.
Holm Security's Next-Gen Vulnerability Management Platform helps you stay one step ahead of cybercriminals by identifying vulnerabilities across your entire attack surface using the latest technology - covering both technical and human assets in everything from traditional infrastructure to the cloud. This helps organizations create a proactive approach towards the modern threat landscape.
What attack vectors are covered in Next-Gen Vulnerability Management?
Next-Gen Vulnerability Management aims to address a holistic view of the organization's security posture by covering a wide range of attack vectors:
- Local and public systems
- Computers
- Cloud infrastructure and resources
- Network equipment
- OT/SCADA
- Web applications
- APIs
- Human assets - your users
How are users a part of Next-Gen Vulnerability Management?
90% of cyber security incidents start with a human element. This makes it obvious that a vulnerability management program must cover the humans - the users.
Through phishing simulation and tailored awareness training, we help your organization build your own human firewall.
Is Attack Surface Management (ASM) covered in Next-Gen Vulnerability Management?
Yes, ASM is often a component of Next-Gen Vulnerability Management, focusing on continuously identifying and assessing external digital exposures to reduce the overall attack surface by identifying blank spots and vulnerabilities.
How do I implement Next-Gen Vulnerability Management?
Implementing Next-Gen Vulnerability Management is efficient and the time to value is short. The implementation, with the help of our experts, just takes a few days.
Talk to one of our cyber security experts to learn how you can get started today with Next-Gen Vulnerability Management.
What is the benefit of Next-Gen Vulnerability Management?
Next-Gen Vulnerability Management helps you strengthen your cyber security defense and, at the same time, save both time and money.
Summarized, the benefits of Next-Gen Vulnerability Management:
- Unparalleled attack vector coverage
Comprehensively safeguard your entire IT infrastructure. - Attack Surface Management
Ensure comprehensive protection by staying informed and up-to-date across your attack surface. - Smart threat intelligence
Assists you in strategically managing your organization's risk exposure. - True unification
A unified view for comprehensive risk management, streamlining prioritization, and effective remediation.
How does Next-Gen Vulnerability Management compare to traditional vulnerability management?
Traditional vulnerability management has been a cornerstone of a robust cyber security strategy for about 25 years. It enables organizations to identify and mitigate security risks proactively. However, traditional vulnerability management has limitations and doesn't meet the current threat landscape.
- Focuses on technical vulnerabilities in a limited number of attack vectors (systems and web applications) and overlooks human-centric attack vectors, including employees.
- Lack of context, or threat intelligence, to better understand and prioritize vulnerabilities.
- Requires considerable time and resources, making it a less-than-ideal solution for organizations with limited capabilities.
- Products that cover different attack vectors operate in silos without any integration.
- The lack of coordination among these tools leads to increased operational costs and diminished productivity.
How do I get started with Next-Gen Vulnerability Management?
BLOG
Modernizing vulnerability management for full attack surface coverage
Next-Gen in our Knowledge Base
If you're already a customer and want to get the most out of Next-Gen Vulnerability Management in practice, please navigate to our Knowledge Base and explore related articles and our Next-Gen Roadmap.

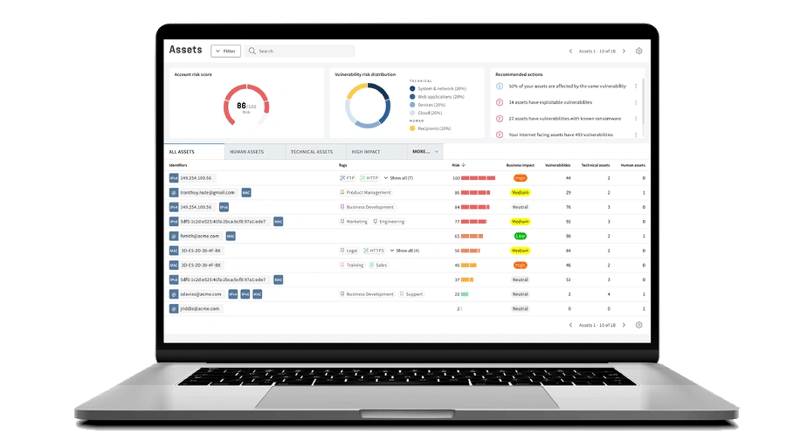
How unification removes complexity from vulnerability management
In this webinar, we'll explore a solution to the growing number of attack vectors: the Unified Vulnerability Management Platform. It streamlines security by consolidating assets into one platform, simplifying workflows, and reducing complexity. Say goodbye to product juggling, extensive training, and unnecessary complications.

Complete asset coverage: How to improve your defenses against Cyberattacks
This webinar will cover how to ensure your cyber security defense is set up correctly for each asset type and better prepare you with an action plan to better stop all types of attacks.
