A breakdown of NIS2 sectors and their entity classifications
The NIS2 Directive encompasses a multitude of sectors and your organization may fall under the NIS2 umbrella depending on sector and criticality.
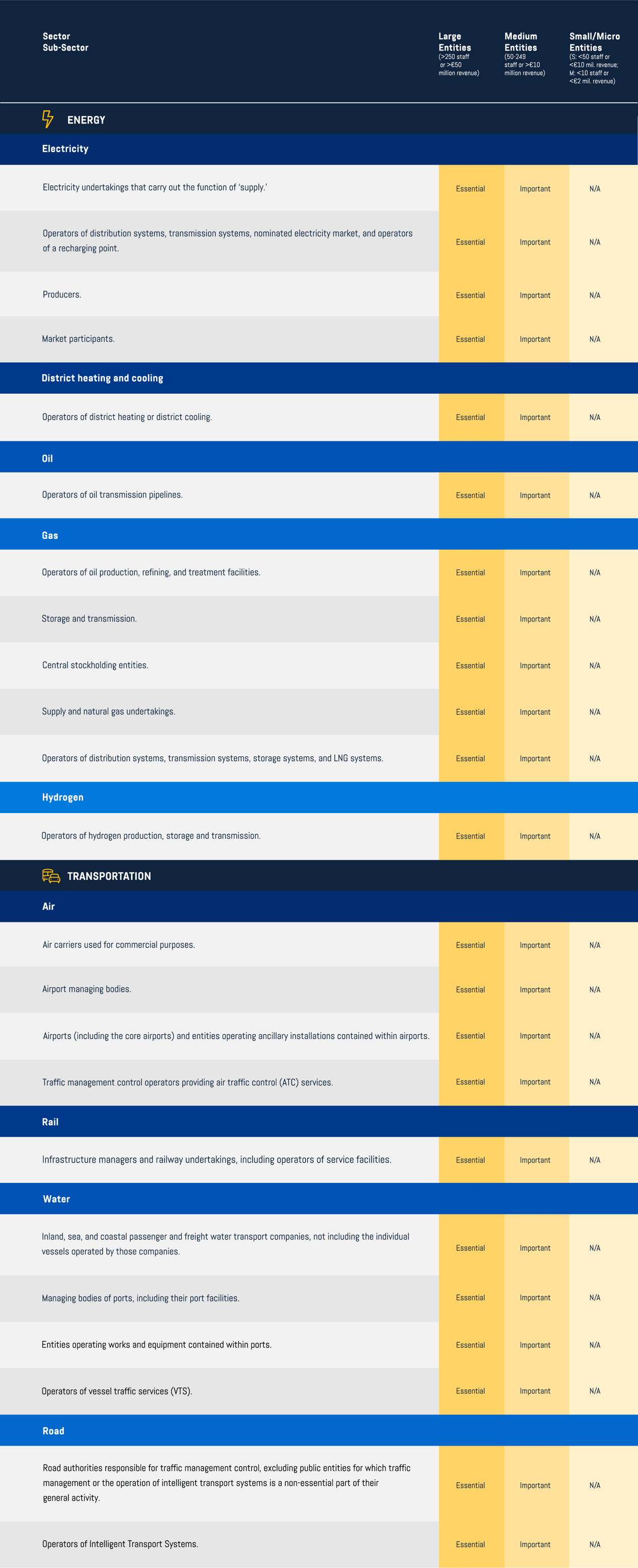
Sectors of high criticality
NIS2 Directive: Annex 1
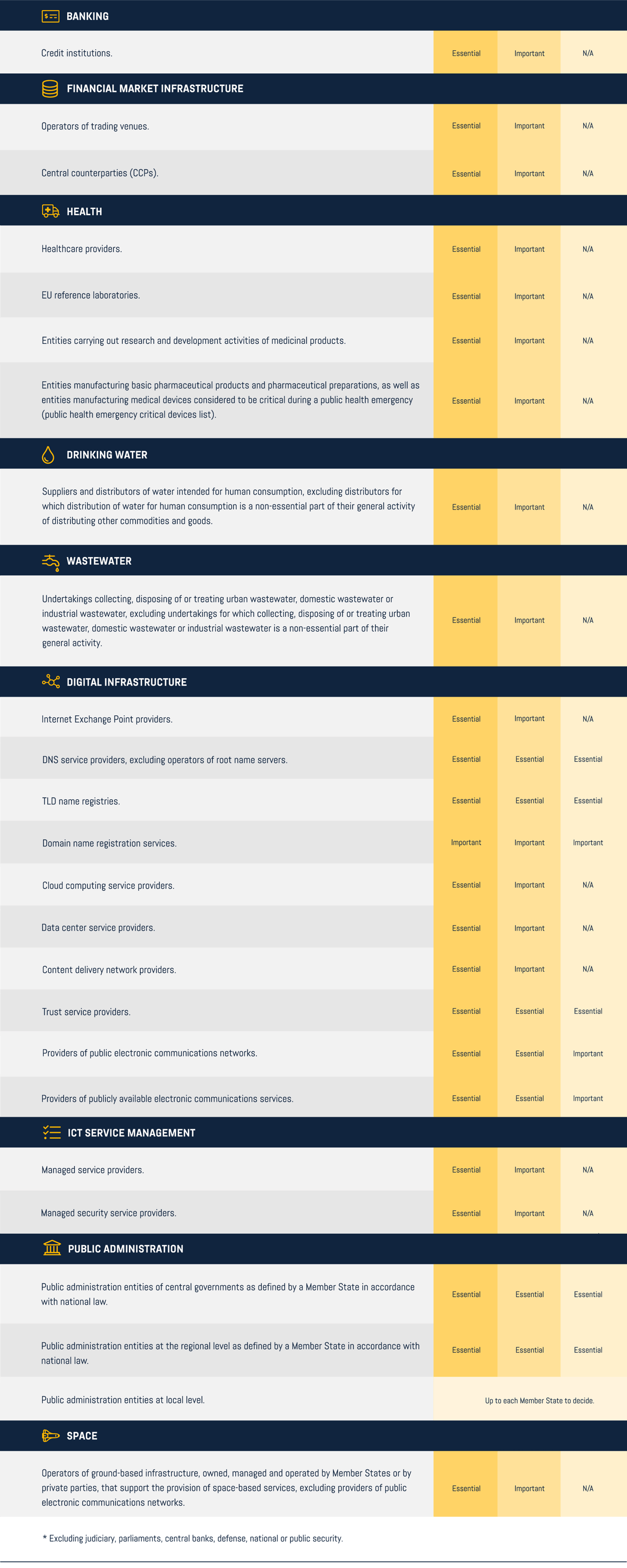
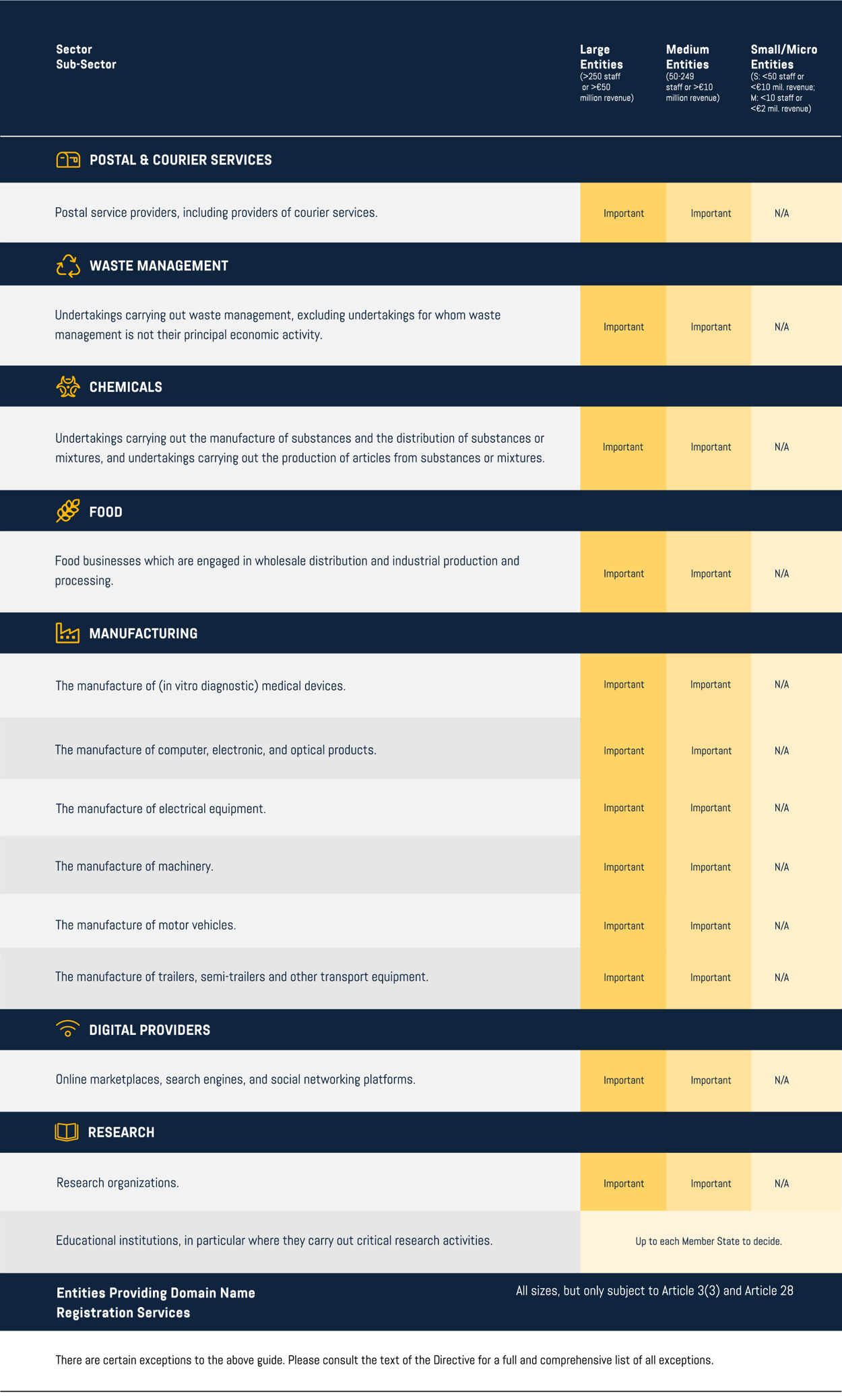
Other critical sectors
NIS2 Directive: Annex 2










.png)
Download our
NIS2 Reference Guide
Getting you ready for NIS2 compliance

What is NIS2 & how will it affect your organization?
Under the NIS2 Directive, more entities and sectors will be required to take steps that will aid in improving cyber security in Europe. In addition to addressing supply chain security, NIS2 streamlines reporting obligations introduces stricter supervisory measures, and introduces more enforcement requirements.

How the NIS2 Directive will impact you
As part of this webinar, we will be joined by Anders Jonson, a cyber security expert and Senior Advisor at ENISA, who has been involved in the development of NIS2 for the EU.

NIS2 Reference Guide: Securing critical infrastructure
Our NIS2 Reference Guide is packed with essential insights and lays out actionable steps for organizations to take for compliance.
We'll help you comply with the NIS2 Directive.
Get started today.

