Safeguarding Your Patient's Data with Next-Gen Vulnerability Management
The relentless wave of cyber threats looms, with hospitals and healthcare organizations finding themselves prime targets. In the critical battle for data security and patient safety, our platform empowers healthcare institutions to shield patient data from prying cybercriminals and drastically reduce the risk of potentially life-threatening sabotage. Together, let's fortify the healthcare sector and ensure the well-being of both lives and health.
Protecting Daily Operations from Cyber Threats
Data Breaches & Patient Privacy
Your organization likely holds vast amounts of sensitive patient information, such as medical records and personal data. Protecting this data from breaches and unauthorized access is a major challenge. Data breaches not only compromise patient privacy but also result in regulatory fines and harm to an organization's reputation.
Ransomware Attacks
Healthcare facilities are prime targets for ransomware attacks. These attacks can encrypt critical patient data, disrupt hospital operations, and demand large ransom payments for decryption keys. Ransomware attacks not only pose a financial burden but can also have life-threatening consequences if patient care is delayed or compromised.
Medical Device Vulnerabilities
Many medical devices, such as infusion pumps and pacemakers, are now connected to the internet for remote monitoring and control. However, these devices often lack robust cyber security measures, making them susceptible to hacking. A breach of a medical device can have serious consequences, including patient harm.


Get Ready for NIS2
In 2024, the NIS2 directive will usher in more stringent cybersecurity requirements across the EU. For healthcare organizations, this regulatory shift is pivotal. Embracing the directive today is not just a legal obligation but an opportunity to bolster your reputation, earn the trust of patients and foster growth and profitability.
-
Unleash the Power of Risk Assessment
Prioritize security gaps and stay ahead of evolving cyber threats. Our platform offers incident reporting for both security incidents and vulnerabilities, granting you real-time visibility into your healthcare organization's security posture. Proactively identifying trends enables you to safeguard patient data and maintain trust. -
Ensure Business Continuity
Our platform simplifies the identification of vulnerabilities, minimizes risks, and ensures NIS compliance with ease. With just a few clicks, you can navigate the intricate landscape of healthcare cybersecurity. By doing so, you can focus on what truly matters – providing uninterrupted patient care while safeguarding sensitive medical information.

GDPR Compliance Made Simple
Hospitals and healthcare organizations deal with vast troves of patient data, intensifying the need for stringent data protection. The GDPR (General Data Protection Regulation) mandates this safeguarding, imposing hefty fines for data breaches that can compromise both finances and patient well-being. Our platform empowers your security team to efficiently mitigate risks, pinpoint and fortify systems housing sensitive data, and safeguard against GDPR-related penalties.
-
Prioritize Personal Data Systems
To fortify your defenses, tag systems processing personal data as high-priority assets, elevating their risk scores. This strategic move ensures vulnerabilities in these critical assets take precedence for remediation, minimizing exposure and potential GDPR violations. -
Keep Tabs on the Remediation Progress
Integrate with ticketing solutions like JIRA and ServiceNow to seamlessly fold remediation into your IT team’s existing workflow and ensure SLAs are met, and GDPR systems are patched in a timely manner.

Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes critical components like electronic health records systems, medical devices, and patient-facing mobile applications, which often extend across multiple locations and pose unique challenges that traditional security tools may not address effectively. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
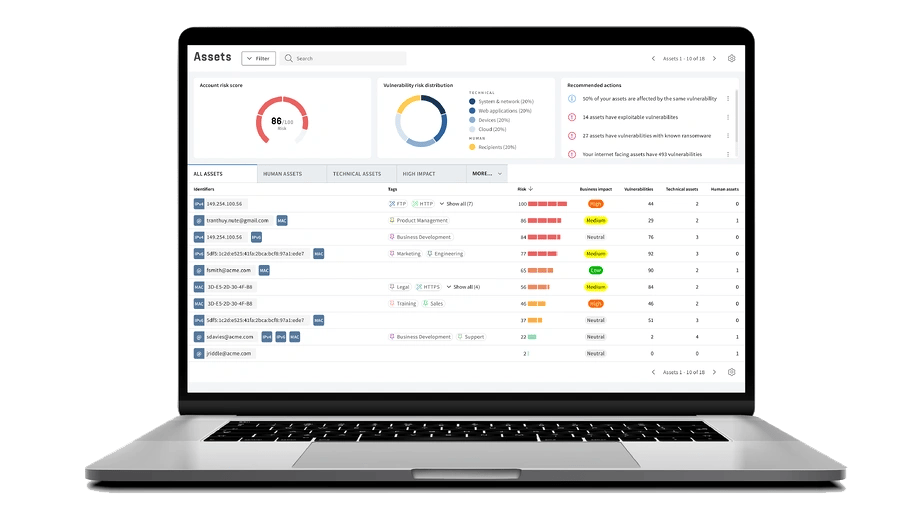
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving the healthcare sector, and understanding the specific challenges and risks you face. Our solution is designed to tackle the vulnerabilities inherent in your industry.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your production processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.

It's extremely important that the Vulnerability Management tool we use is meticulous and detailed but also generates clear and visual reports – so that it’s easy for us to take action. Holm Security VMP makes it easy for us to prioritize critical vulnerabilities and has become absolutely essential for us.
Andras Szabo
CIO at WESSLING HungaryLatest news

5 ways to create a successful vulnerability management program
A successful vulnerability management program requires these 5 key components.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.




