Elevate Data Security & Privacy with
Next-Gen Vulnerability Management
Navigating compliance and risk management in finance comes with the threat of harsh penalties and reputational harm. The digital landscape adds complexity, highlighting the importance of data security and privacy. Let Next-Gen Vulnerability Management from Holm Security be your partner in navigating the digital frontier, helping you to turn these challenges into opportunities for enhanced security, improved compliance, and unrivaled customer trust.


PCI Compliance Made Simple
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
Make Compliance Documentation Easier
Simplifies the work of documenting compliance status with out-of-box scan and reports templates. Saving you time and effort. -
Increase Efficiency
Utilize security risk assessment to quickly identify and prioritize vulnerabilities and misconfigurations.

Get Ready for DORA
Achieving operational resilience through DORA and effectively assessing cyber risks requires a methodical, step-by-step approach. It's not enough to simply check off boxes. Holm Security can assist in streamlining and simplifying this process.
-
Prioritize Security Gaps from a Risk-Based Perspective
Prioritize security gaps and address new risks continuously to stay ahead of cyber threats. Our platform offers incident reporting for incidents and vulnerabilities, allowing you to monitor your security and proactively identify trends. -
Stay Ahead of Potential Threats
Our platform enables you to easily identify vulnerabilities, minimize risk, and maintain compliance with just a few clicks. We assist in monitoring potential threats, providing peace of mind that your systems and data are secure at all times.

See For Yourself
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic assets such as cloud-based banking software, remote devices and mobile banking apps that can be located anywhere and often fall outside the scope of traditional VM tools. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
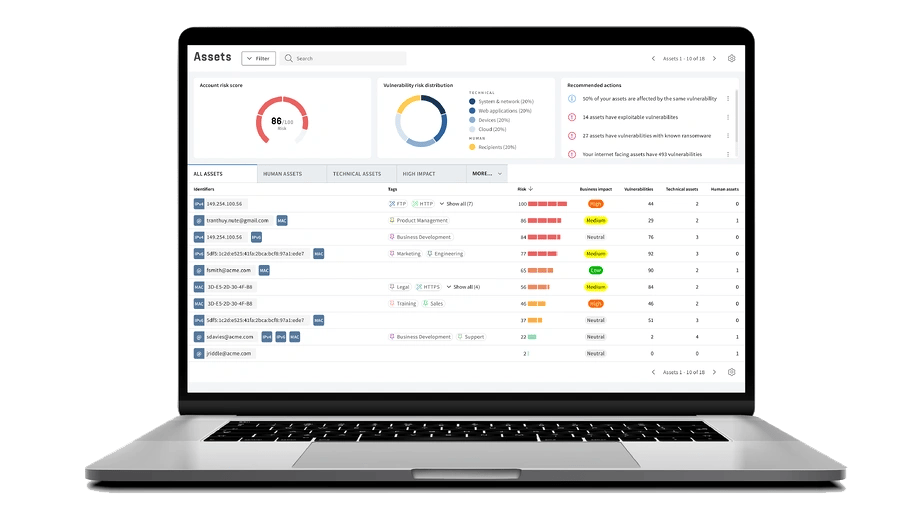
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point that a cybercriminal could take advantage of. Efficiently monitor and manage all of your systems, applications, endpoints, and employees for weaknesses.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that put your organization at risk from cybercriminal attacks vs. the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk assessment in real-time right from your one-view assets dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest news

5 ways to create a successful vulnerability management program
A successful vulnerability management program requires these 5 key components.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.



