Cyber-Resilient From Farm to Table with Next-Gen Vulnerability Management
In the interconnected food supply chain, a minor hiccup during the harvest season can cause major consequences for processing plants and distribution networks. Safeguard crucial systems and ensure food reaches tables with our tailored Vulnerability Management Platform. Choose safety, resilience, and peace of mind with Holm Security.
Combatting Cyber Risks in the Food Chain
Legacy Systems
Supply Chain Complexity
With an intricate supply chain, it can be challenging to ensure comprehensive security, particularly for small organizations operating on tight margins. Leave no entry point open for cybercriminals, and use our platform to verify your suppliers' cyber security defense.
IoT Devices
Limited Budget


Get Ready for NIS2
In 2024, NIS2 will set a new cybersecurity benchmark for the food sector across the EU. We'll help you enhance your security posture, secure customer trust, and ensure compliance.
-
Unleash the Power of Risk Assessment
Prioritize security gaps and address new risks continuously to stay ahead of cyber threats. Our platform offers incident reporting for incidents and vulnerabilities, allowing you to monitor your security and proactively identify trends.
-
Ensure Business Continuity
Our platform enables you to easily identify vulnerabilities, minimize risk, and maintain compliance with just a few clicks. With our help, you can navigate the complexities of NIS compliance with ease, leaving you free to focus on what really matters - growing your business.

GDPR Compliance Made Simple
With Holm Security, you can get a comprehensive assessment of vulnerabilities across your entire attack surface. Our solution can help your security team to efficiently reduce risks. Identify and safeguard systems that store and use sensitive data, preventing GDPR fines.
-
Prioritize Systems Handling Personal Data
Tag specific systems that process personal data as more important than other systems, amplifying the risk score of the asset and ensuring that the vulnerabilities found on these assets are prioritized for remediation.
Keep Tabs on the Remediation Progress
Integrate with ticketing solutions like JIRA and ServiceNow to seamlessly fold remediation into your IT team’s existing workflow and ensure SLAs are met, and GDPR systems are patched in a timely manner.

Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic assets such as supply chain logistics, food production facilities, and mobile food delivery apps that operate across diverse locations and often fall beyond the scope of traditional security tools. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
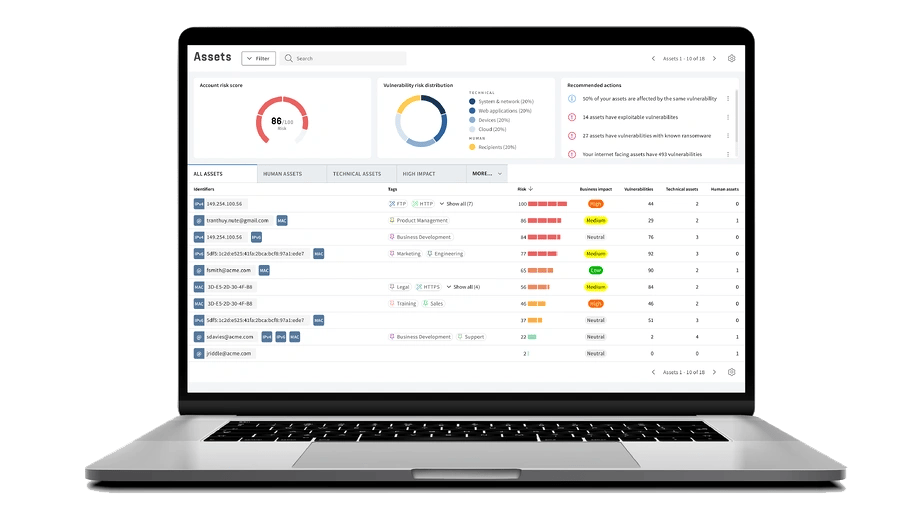
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Holm Security?
Industry Expertise
Our solution is designed to tackle the security challenges inherent in your industry, providing a robust shield against both existing and emerging threats.
Seamless Experience
Integrate our solution seamlessly with your current setup and experience robust protection to ensure uninterrupted business operations.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest news

5 ways to create a successful vulnerability management program
A successful vulnerability management program requires these 5 key components.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.



