Keep Your Consumers Secure with Next-Gen Vulnerability Management
The retail sector has been the target of some of the most high-profile data breaches in recent years, which can result in severe damage to trust and significant economic loss. The rise of digitalization has only made the industry more susceptible. Let Next-Gen Vulnerability Management from Holm Security be your partner, helping you to turn challenges into opportunities for enhanced security, improved compliance, and unrivaled customer trust.
Protecting Your Business from Cyber Threats
Customer Data
Retail businesses handle significant amounts of customer data, including Personal Identifiable Information and Credit Card details necessary for transactions. This data is highly valuable to hackers, who can exploit it to launch further attacks, sell it on the dark web, or make unauthorized purchases.
Take Proactive Measures Against Ransomware
As a retailer, it's important to take proactive measures against ransomware attacks. Unfortunately, these types of attacks are becoming more common and can result in the complete lockdown of central systems and cash registers in physical stores.
Internet of Things (IoT)
Every connected device dramatically increases the organization’s attack surface. Although security software is typically included with Internet of Things (IoT) devices, it is often insufficient. Hackers can easily exploit the numerous vulnerabilities of IoT devices to infiltrate retail security systems and obtain unauthorized access to confidential information.



Achieve PCI DSS Compliance
Protecting Customer Data & Data Transparency
Retailers process and store large amounts of personal data for many different purposes. Not least as a result of the physical world becoming more and more integrated with the digital world.
GDPR (General Data Protection Regulation) increases demand to secure all systems storing or processing personal data. Accordingly, the challenge of protecting this data is becoming more extensive. Membership systems, self-scan, and self-checkout significantly increase the amount of personal data processed and stored.
Get Ready for NIS2
Under NIS2, certain retail areas are also included under “operators of essential services and important entities” that have “food production, processing and distribution.”
-
Safeguard Public Services
Through our platform, effortlessly pinpoint vulnerabilities, diminish risks, and uphold NIS2 compliance. By alleviating the intricacies of cybersecurity compliance, municipalities can invest more time and resources in enhancing community services and development.
-
Ensure Business Continuity
Stay a step ahead of potential cyber threats. Our platform provides continuous security gap prioritization and features incident and vulnerability reporting. This enables your municipality to proactively monitor your security landscapes and discern patterns.
Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic assets such as online storefronts, customer data repositories, and e-commerce mobile apps that can be located anywhere and often fall outside the scope of traditional management tools. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
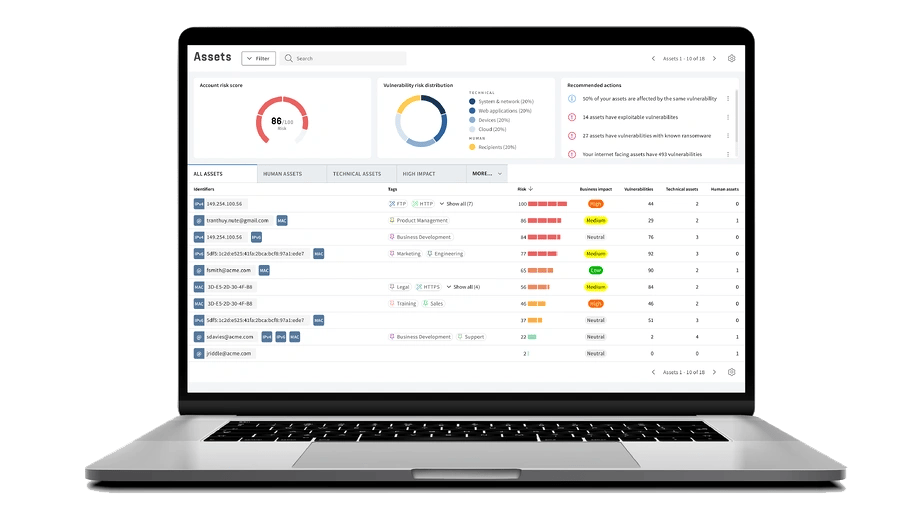
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving retailers and e-commerce and understand the specific challenges and risks you face. Our solution is designed to tackle the vulnerabilities inherent in your industry.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your existing processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest news

5 ways to create a successful vulnerability management program
A successful vulnerability management program requires these 5 key components.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.





