Exposure & risk management for a proactive cyber defense
Is fragmented visibility leaving you exposed to cyber threats? Our platform is built to provide a broader and more comprehensive insight into your exposures.
The uphill battle for your security team
Large product stack & silos
Many organizations have built a large stack of cyber security products to meet increasing challenges within the industry. These products run in silos, creating a fragmented view of their attack surface.
Lack of
context
The lack of a unified risk model and the need to jump between different platforms make it difficult for security teams to get a complete overview of their security posture and prioritize remediation tasks.
Costly & less secure
A large tech stack, product silos, and a lack of unification make security work less efficient, exposing your organization to unnecessary risk and costs.
Watch our platform demo
Our market-leading platform is the cornerstone of a proactive cyber defense, empowering you to always stay one step ahead of cybercriminals.
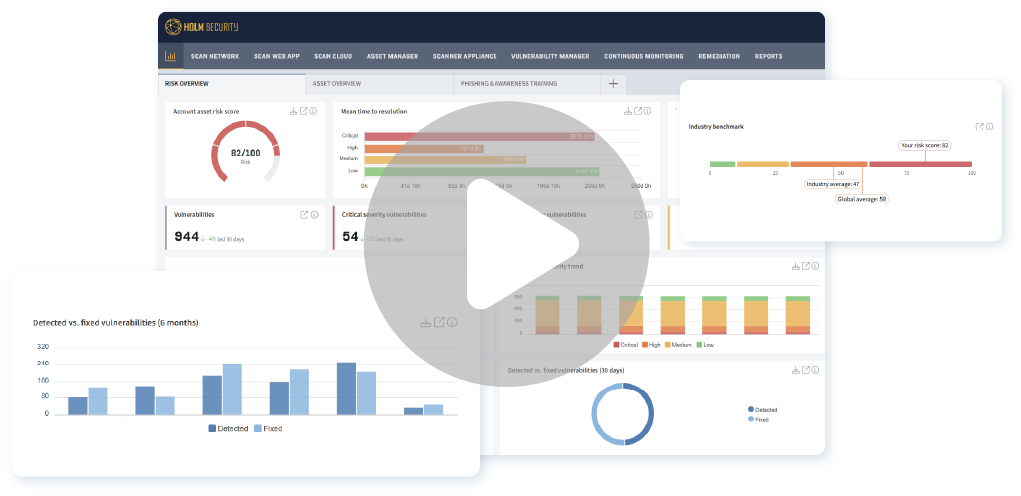
Get proactive with exposure management
One platform – one risk model
Our platform is not a mix of different technologies and legacy systems topped with a dashboard. Our platform was designed from the start with unified product integration in mind.
Gain insight into your attack surface
Discover assets in your IT infrastructure automatically and continuously.
Comprehensive attack vector coverage
We provide a complete attack vector coverage, including systems/servers, computers, Kubernetes clusters, IoT, OT, cloud-native platforms, users, and more.
AI-driven threat intelligence
Our AI-powered Security Research team keeps you updated with the latest vulnerabilities 24/7, all year round.
Enable efficient risk communication
Accurately communicating risk allows stakeholders to take action that drives business value.
A unified platform built for exposure management – from the very beginning

System & Network Security
Identifying over 200,000 vulnerabilities across business-critical systems/servers, computers, network devices, office equipment and IoT, OT (Operational Technology), and cloud platforms.

Web Application Security
Advanced assessment technologies to identify thousands of vulnerabilities, including OWASP Top 10, in modern web applications.

Cloud Security (CSPM)
Secure your cloud-native platforms by identifying thousands of vulnerabilities across Microsoft Azure, Microsoft 365, AWS, Google Cloud, and Oracle Cloud — providing proactive protection for your entire cloud ecosystem.

API Security
Assess your APIs for hundreds of vulnerabilities, including those in the OWASP API Top 10, to ensure robust security and safeguard critical data.
Phishing Simulation & Awareness Training
Conduct simulated phishing attacks paired with customized awareness training to build continuous vigilance and strengthen your human firewall.

Meet today's & future compliance
NIS & NIS2
The NIS and NIS2 Directives require a systematic and risk-based cyber security approach. Holm Security has helped hundreds of organizations comply with the NIS Directive and now does the same with NIS2.
GDPR
Our platform helps organizations meet General Data Protection Regulation (GDPR) requirements for regular security assessments and vulnerability testing to identify and address potential vulnerabilities and protect against data leakage.
ISO 27001
To comply with ISO 27001, an organization must establish and maintain an Information Security Management System (ISMS) that meets the standard's requirements. This includes continuous risk assessments to find vulnerabilities.
PCI DSS
We provide Payment Card Industry Data Security Standard (PCI DSS) compliance scanning for payment card processing environments that meet the security standards set by PCI DSS. Our platform is listed as an Approved Scanning Vendor (ASV) in cooperation with our partner Akati.













Your trusted partner

Frequently asked questions
What is exposure management and how is it different from vulnerability management?
Exposure management is a continuous cyber security practice that identifies, prioritizes, and reduces potential asset exposure across an organization’s attack surface. Unlike traditional vulnerability management, which focuses mainly on known software flaws (e.g. CVEs), exposure management provides a broader, risk-based approach. It includes vulnerabilities, misconfigurations, identity risks, insecure protocols, and unmonitored assets such as shadow IT.
How does Holm Security work with exposure management?
From the very beginning, Holm Security has done vulnerability management differently, calling it Next-Gen Vulnerability Management. Today, the term “exposure management” is becoming more widely used, and is in effect Next-Gen. This means that our platform does what many call exposure management.
We provide:
- A risk-based approach to cyber security.
- Broader attack vector coverage.
- Attack Surface Management (ASM) and External Attack Surface Management (EASM).
- Threat intelligence beyond CVSS and severities to support efficient prioritization.
- Complete workflow support.
- A single pane of glass.
- A platform that helps you reach and maintain compliance.
What products are included in exposure management?
Reach out to our Sales team to learn which solutions, such as ASM and EASM, and features come with each product.
How do I get started with exposure management?
There are many ways to get started, all of which are quick and easy. You can request a meeting, quote, or a free trial, or reach out to our Sales team.
