DORA (Digital Operational
Resilience Act)
The financial sector plays a vital role in our economy but is prone to cyber threats. The European Union has introduced the Digital Operations Resilience Act (DORA) to mitigate these risks. This act aims to establish a standardized approach to managing Information and Communication Technology (ICT) by enforcing governance, risk management, and incident reporting regulations. The implementation of these rules will enhance protection against cyberattacks and contribute to the growth of our digital economy.
Strengthening Operational Resilience in the Financial Sector
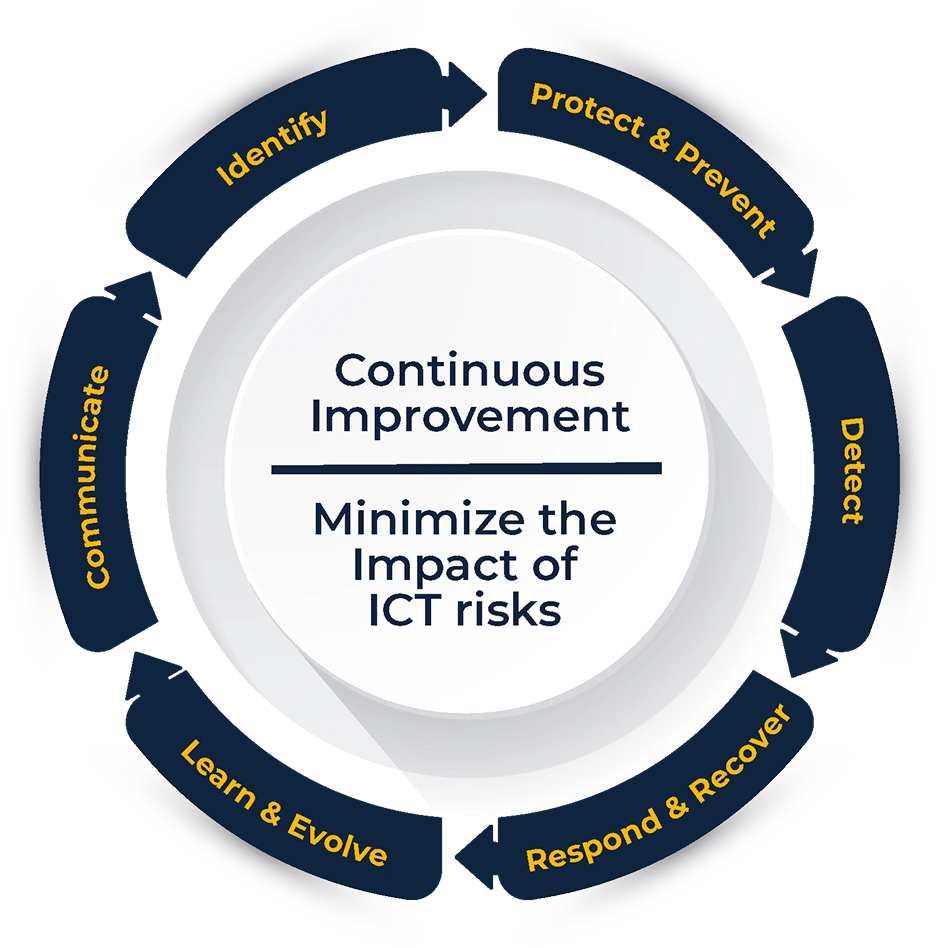
- DORA mandates that financial institutions manage all aspects of operational resilience, including protection, detection, containment, recovery, and repair capabilities against ICT-related incidents.
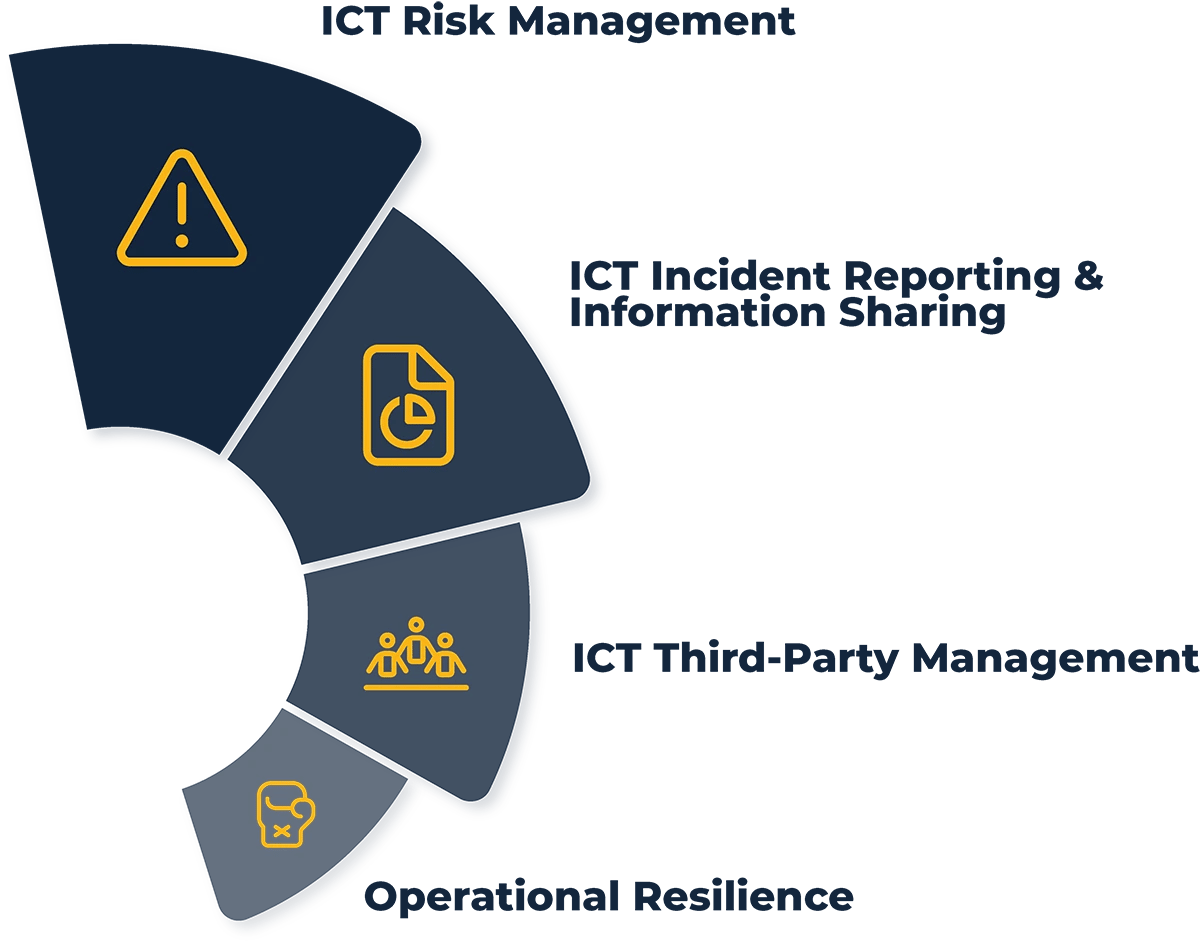
- DORA establishes guidelines for ICT risk management, incident reporting, operational resilience testing, and ICT third-party risk monitoring.
- The regulation recognizes that a lack of operational resilience and ICT incidents can threaten the financial system's stability, even if adequate capital exists for traditional risk categories.
What is Applicable?
EU Regulation
DORA will enter into force as a new regulation at the European level and must be applied equivalently in all EU countries.
Timeframe
DORA was hammered out in January 2023 and has a 24-month implementation period. Organizations, where DORA applies, must be ready at the latest January 2025.
Penetration Testing
Article 23 and article 24 (threat-based penetration tests) will only come into force 36 months after the regulation's publication date.
We'll Help You Comply with Digital Operational Resilience Act
Start your compliance journey now.
Secure your Digital Operational Resilience
Financial institutions need to comply with DORA by doing the following:
- Review and improve the resilience level of their current ICT landscape.
- Update their internal policies, procedures, and governance and control framework to implement DORA's requirements. The management body must define, approve, oversee, and ultimately be responsible for this.
- Establish an ICT-related incident management process to detect, track, log, categorize, classify, and notify ICT-related incidents in accordance with DORA.
- Ensure that any contractual (outsourcing) arrangements comply with DORA.
Key Obligations of DORA




Charting a Course through the Sea of ICT Risks
- Install and maintain resilient ICT systems and tools that minimize the impact of ICT risks.
- Identify, classify and document mission-critical functions and assets.
- Continuously monitor all sources of ICT risks in order to take preventive protection measures.
- Ensure immediate detection of abnormal activities.
- Put in place an adapted and comprehensive business continuity policy with crisis and recovery plans, including annual testing of the plans, covering all supporting functions.
- Establish mechanisms to develop and learn from external events as well as the company's own ICT incidents.
Reporting ICT-related Incidents in Financial Companies
Financial companies are obliged to:
- Develop an agile process to log/classify all ICT incidents and determine major incidents according to the criteria in the regulation and further specified by the European supervisory authorities (EBA, EIOPA, and ESMA).
- Submit an initial, interim, and final report on ICT-related incidents.
- Adapt the reporting of ICT-related incidents through standard templates developed by ESA.
Adherence to Annual Digital Operational Resilience Testing Protocols
- Annually perform basic tests of ICT tools and systems.
- Identify, prevent, and immediately eliminate any weaknesses, deficiencies, or gaps in the implementation of countermeasures.
- Regularly perform advanced penetration tests (TLPT) for ICT services that affect critical functions. Third-party ICT service providers must participate and fully cooperate in the testing activities.
Navigating the Wild World of Third-party ICT Services
- Ensure control of risk arising in connection with ICT services from third-party providers.
- Report all outsourced activities and all changes that occur regarding critical ICT services from third parties; take into account IT risks that may arise when hiring subcontractors; merge essential parts of the ICT services and third-party provider relationships for complete monitoring.
- Ensure that the contract with the third-party provider of ICT services has a detailed and full information service level, where data is handled etc.
- Business-critical third-party providers of ICT services fall under the so-called Union Oversight Framework, which can issue recommendations to reduce ICT risks. Financial companies must consider the risks associated with third-party providers who do not follow the guidance.
Preparing for the Digital Operational Resilience Act
Anticipate Disruption
To become operationally resilient, companies must first acknowledge that disruptive events are inevitable. Preparation is critical to being able to withstand disruptions that will inevitably occur.
Coping with Third-Party Risks
Third-party suppliers' risks evolve with their products and services. Relying only on yearly assessments will result in a loss of control. To maintain control, financial entities should continuously assess their third-party ecosystem.
A Multidisciplinary Approach
By adopting a unified and dynamic approach and a framework encompassing all domains, businesses can achieve advanced operational resilience even in a fast-paced environment where new risks emerge regularly.
Safeguard Your Business from Cyberattacks
Extend Visibility
Know what you're up against. We can help you identify your IT system's weak points, categorize the assets that are vulnerable, and pinpoint the most likely threats. This knowledge will help you take action to protect your business proactively.
Prioritize Action
Identifying risks is just the first step; you need to act on them. We can help you develop a clear action plan that prioritizes your actions based on the level of threat, potential impact, and resources.
Communicate Risk
Don't keep cyber security risks a secret - communication is key. Get a clear view of your business's cyber risk with Holm Security. Our platform provides security executives and business leaders with centralized and business-aligned insights, including actionable insights into your overall cyber risk.

Ready to Navigate DORA Compliance?
Book Your Consultation Meeting Today!
What You Need To Know
As an ICT service provider in the supply chain, what direct or indirect effects will DORA have on my business?
If you're an ICT service provider in the supply chain, DORA may affect you. DORA aims to improve cyber security and resilience in the financial sector, including ICT service providers like you. This will indirectly impact you in terms of contracts and compliance requirements. Financial entities will review their contract agreements with you, so you should ensure your contracts align with DORA requirements. You'll be subject to DORA and other oversight requirements and are considered a critical supplier. To comply, you must work closely with financial entities and ensure all DORA requirements are met.
Which law prevails between DORA and NIS2?
When it comes to digital finance, many wonders which law prevails between DORA and NIS2. The NIS2 Directive strengthens cyber security requirements across the EU, including for banks and financial market infrastructures. So, which law takes precedence? The answer is simple: DORA is the "lex specialis" of NIS2, meaning that a specific law takes precedence over a general one. In practice, DORA complements and clarifies NIS2 more than it supplants it. According to DORA's Recital 16, "This Regulation constitutes lex specialis concerning Directive (EU) 2022/2555. At the same time, it is crucial to maintain a strong relationship between the financial sector and the Union horizontal cybersecurity framework as currently laid out in Directive (EU) 2022/2555."
Latest news

5 ways to create a successful vulnerability management program
A successful vulnerability management program requires these 5 key components.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.
