Next-Gen Vulnerability Management - welcome to the future
Identify vulnerabilities across your entire attack surface, covering both your technical and human assets, all in one unified platform with one risk model and one workflow.
Efficient, smarter & more complete in the fight against evolving cyber threats
All attack vectors in one place
Identify vulnerabilities and risks in all important attack vectors, including business-critical systems/servers, computers, network devices, office equipment, IoT, OT (Operational Technology), Kubernetes, web applications, cloud-native platforms, APIs and users.
AI-driven threat intelligence
Every risk is enriched by AI for faster and broader coverage of vulnerabilities and extensive threat intelligence, enabling you to focus on the remediation efforts that will most efficiently lower risk exposure.
A single pane of glass
A unified interface offers a comprehensive risk overview, streamlined workflow, and consistent risk model across all attack vectors, enabling teams and individuals to efficiently prioritize and remediate vulnerabilities.
Minimize your attack surface & identify blank spots
Effectively reduce your attack surface by continuously and automatically detecting new assets, tracking asset changes, and uncovering potential blind spots.
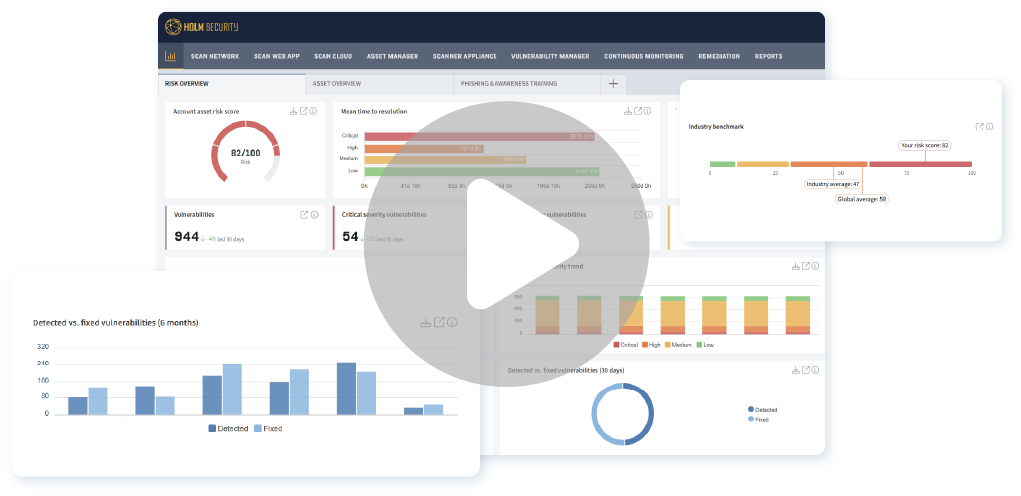
Watch our platform demo
Our market-leading platform is the cornerstone of a proactive cyber defense, empowering you to always stay one step ahead of cybercriminals.
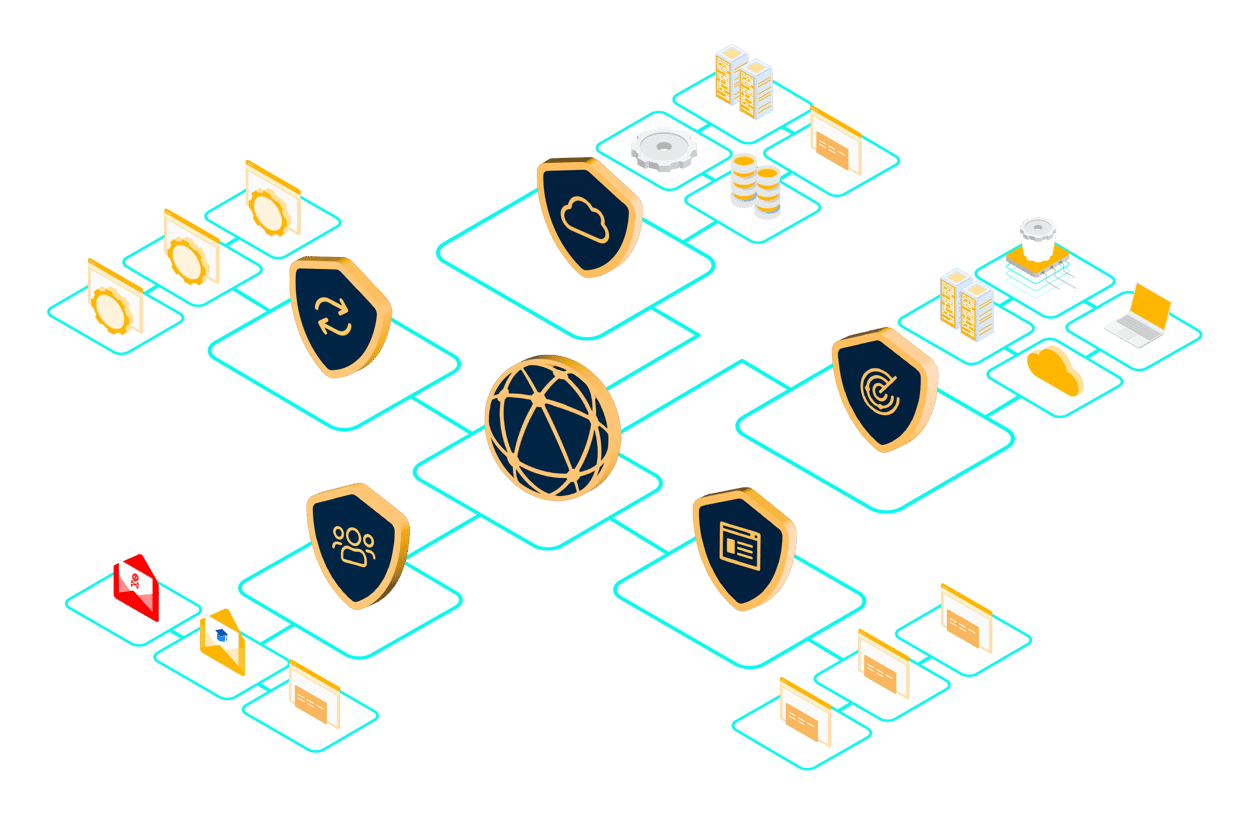
One platform with unified products
Our platform includes powerful products integrated with one workflow and risk model.

System & Network Security
Identifying over 200,000 vulnerabilities across business-critical systems/servers, computers, network devices, Operational Technology (OT), Internet of Things (IoT), Kubernetes, cloud-native platforms, and office equipment.

Web Application Security
Advanced assessment technologies to identify thousands of vulnerabilities, including OWASP Top 10, in modern web applications.

Cloud Security (CSPM)
Secure your cloud-native platforms by identifying thousands of vulnerabilities across Microsoft Azure, Microsoft 365, AWS, Google Cloud, and Oracle Cloud — providing proactive protection for your entire cloud ecosystem.

API Security
Assess your APIs for hundreds of vulnerabilities, including those in the OWASP API Top 10, to ensure robust security and safeguard critical data.
Phishing Simulation & Awareness Training
Conduct simulated phishing attacks paired with customized awareness training to build continuous vigilance and strengthen your human firewall.
Accelerate your cyber defense with
Next-Gen Vulnerability Management
Covering everything from traditional systems to cloud-native platforms
Systems/servers
Business-critical systems, such as Windows and Linux/Unix servers.
Computers
Computers inside your office network and remote computers.
Network devices
Network equipment, including routers, switches, and firewalls.
Office equipment & IoT
Printers, webcams, and other office devices.
Cloud-native platforms
Cloud-native infrastructure in Azure, AWS, Google, and Oracle.
Operational Technology
Supervisory layer for OT (Operational Technology) systems.
Kubernetes
Cloud and on-prem orchestration platform for containers.
Web applications
All types of web applications, both self-developed and commercial applications.
APIs
Application Programming Interfaces (APIs), including REST/OpenAPI, GraphQL, and SOAP.
Users
The human assets in your IT environment.
Get proactive with our
Next-Gen Vulnerability Management Platform
How secure is your organization compared to your industry peers?
Using data from our large customer base across industries, we help you understand your organization’s risk exposure compared to others in the same industry.

Integrated Attack Surface Management (ASM)
Automated from discovery to assessment
Integrated Attack Surface Management (ASM) fully automates the entire process, from asset discovery and continuous monitoring to identifying vulnerabilities.
All features and capabilities in vulnerability management

Meet today's & future compliance
NIS & NIS2
The NIS and NIS2 Directives (entering into effect throughout 2025) require a systematic and risk-based cyber security approach. Holm Security has helped hundreds of organizations comply with the NIS Directive and now does the same with NIS2.
GDPR
Our platform helps organizations meet General Data Protection Regulation (GDPR) requirements for regular security assessments and vulnerability testing to identify and address potential vulnerabilities and protect against data leakage.
ISO 27001
To comply with ISO 27001, an organization must establish and maintain an Information Security Management System (ISMS) that meets the standard's requirements. This includes continuous risk assessments to find vulnerabilities.
PCI DSS
We provide Payment Card Industry Data Security Standard (PCI DSS) compliance scanning for payment card processing environments that meet the security standards set by PCI DSS. Our platform is listed as an Approved Scanning Vendor (ASV) in cooperation with our partner Akati.










.png)
How can we help you?
Your trusted partner

Frequently asked questions
What is vulnerability management?
Vulnerability management is a systematic and ongoing process of identifying, assessing, prioritizing, and mitigating security vulnerabilities in computer systems, networks, software, and hardware. The goal of vulnerability management is to minimize the organization's exposure to security risks by addressing potential weaknesses before malicious actors can exploit them.
Who needs a vulnerability management program?
Vulnerability management helps all organizations, regardless of size and industry/sector, strengthen their cyber defense. According to cyber security frameworks (NIST and ISMSs like ISO 27001), regulations, legislation, and recommendations, vulnerability management is a cornerstone of modern cyber defense.
Why is a vulnerability management program important?
A vulnerability management program is a cornerstone of modern cyber defense. It helps create a systematic and risk-based cyber defense, which is critical to proactively protect your organization from the constantly evolving threat landscape.
How is a vulnerability management program important in relation to frameworks and regulations?
The future is characterized by a growing number of compliance demands focusing on systematic and risk-based cyber defense —and this is exactly what vulnerability management is about. NIS, NIS2, DORA, CRA, GDPR, ISO 27001, and PCI DSS are a few regulations that specifically point out vulnerability management as an important solution for cyber defense.
What is the difference between traditional vulnerability management and Next-Gen Vulnerability Management?
Traditional vulnerability management covers a limited number of technical attack vectors, such as systems and web applications, while Next-Gen Vulnerability Management covers everything from traditional systems to cloud-native platforms, OT, IoT, devices and your users.
Next-Gen Vulnerability Management comes with several additional advantages:
- A single pane of glass – one workflow and one risk model
- AI-driven threat intelligence – enriching vulnerabilities with critical intelligence related to, for example, ransomware
Is Attack Surface Management (ASM) included with Holm Security’s Next-Gen Vulnerability Management Platform?
ASM and External Attack Surface Management (EASM) are included and integrated with our Next-Gen Vulnerability Management Platform.
How long does it take to get started?
Getting started takes just a few hours. Contact us, and we will help you get started today.
What integrations are available?
We provide native integrations and custom integrations using our platform API. Read more about integrations here.

