The market-leading
platform for a
proactive cyber defense
Our market-leading Next-Gen Vulnerability Management Platform (VMP) is the cornerstone for a proactive cyber defense, empowering you to always stay one step ahead of cybercriminals.




















Next-Gen Vulnerability Management vs. traditional
Efficient, smarter & more complete in the fight against evolving cyber threats
Holm Security’s Next-Gen Vulnerability Management Platform (VMP) sets the foundation for a systematic, risk-based, and proactive cyber defense against threats that can cause financial and reputational damage to your organization, such as ransomware and phishing.
Our platform efficiently combines attack surface management (ASM/EASM) and vulnerability management to understand and minimize your attack surface and detect vulnerabilities before they are exploited by cybercriminals.
Unparalleled attack vector coverage
Holm Security’s Next-Generation Vulnerability Management Platform (VMP) covers multiple attack vectors, from traditional systems and computers to cloud-native platforms.
Integrated Attack Surface Management (ASM)
With Attack Surface Management integrated into the platform, you will automatically discover new assets and monitor existing ones, eliminating the risk of blank spots and shadow IT.
AI-driven threat intelligence
We use AI for faster and broader coverage of vulnerabilities, additional threat intelligence, and data enrichment for every vulnerability, enabling you to focus on the risks that will most efficiently lower risk exposure once remediated.
Fully automated
Our platform is fully automated. Once implemented, it runs automatically and continuously in the background to ease administration, suitable for IT teams big and small.
The modern attack surface has outgrown traditional vulnerability management
Incorporating modern technologies in day-to-day operations presents a broader range of attack vectors for potential exploitation. The attack surface has expanded, making traditional vulnerability management methods insufficient in dealing with these sophisticated attacks. The scope of vulnerability management needs to extend beyond just systems and web applications to include other critical components such as network infrastructure, cloud services, mobile devices, and even IoT (Internet of Things) devices.
Limited attack vector coverage
Scanning only your systems and web apps may leave blind spots and hidden vulnerabilities in your infrastructure, leaving a considerable attack surface unprotected.
Out of context risks
Not all vulnerabilities are created equal. Traditional vulnerability management doesn't take into account how each vulnerability relates to the unique aspects of your organization’s operations, assets, or threat landscape.
Too many tools & silos
Over time, many organizations have built up a significant product stack, relying on multiple tools and products that are not integrated - costly and often require additional effort to interpret the findings.
No Attack Surface Management
To understand what to protect, you must first understand your attack surface. Traditional vulnerability management only has limited support for Attack Surface Management (ASM).
Next-Gen Vulnerability Management Platform
Market-leading coverage of systems & networks
Identifying over 100,000 vulnerabilities in business-critical systems/servers, computers, network devices, office equipment and IoT, Operational Technology, and cloud platforms.

Efficiently minimize risk in modern web applications
Advanced assessment technologies to identify thousands of vulnerabilities, including OWASP Top 10, in modern web applications.

Find vulnerabilities & misconfigurations in your cloud-native platforms
Secure your cloud-native platforms by identifying thousands of vulnerabilities in Microsoft Azure, AWS, Google Cloud, and Oracle Cloud.
.png?width=1200&height=795&name=CS%20blueprint%20(2).png)
Secure your APIs to protect your business-critical data
Assess your APIs for hundreds of vulnerabilities, including the OWASP API Top 10, to ensure their security and protect critical data.

Create user resilience & awareness to build your human firewall
Run simulated phishing attacks with tailored awareness training for continuous awareness, effectively building your human firewall.

Market-leading vulnerability coverage
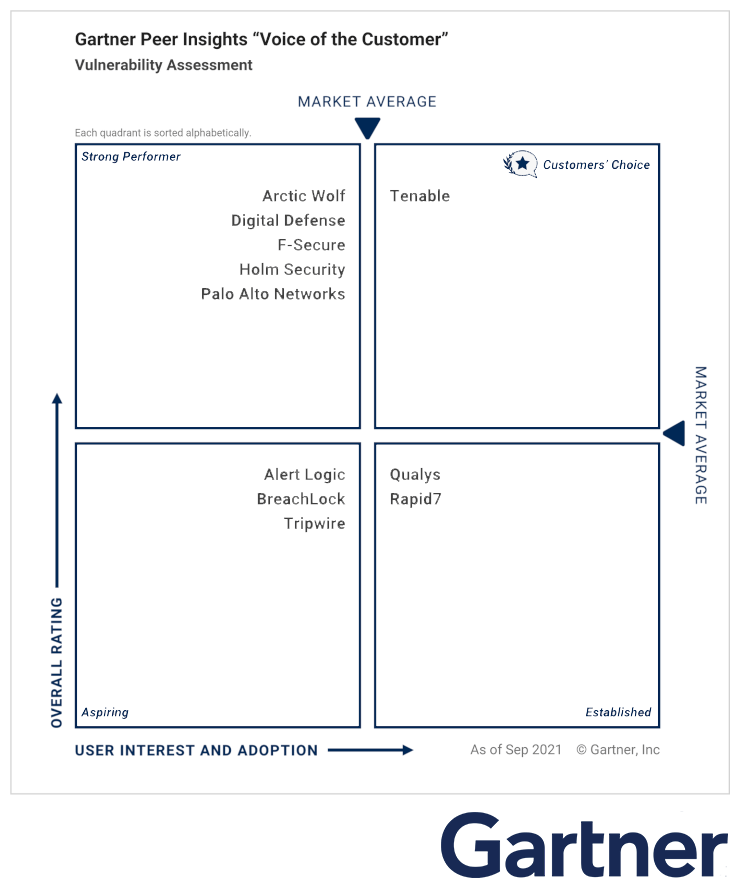
Gartner Voice of the Customer
Holm Security is pleased to announce our inclusion in Gartner's "Voice of the Customer" report. This report is based on reviews from Gartner Peer Insights, which recognizes vendors and products highly rated by their customers. Our success is attributed to our ability to effectively address our customers' needs. To fully understand the extent of our achievements, we encourage you to read the individual reviews and ratings shared by our satisfied customers on Gartner Peer Insights.
Get started with a
proactive cyber defense
Your tailored vulnerability management
solution is 3 steps away
Book a
meeting
During the initial call, our team will get an understanding of your business technology status and needs.
Book a meeting here.
Get your custom solution
Our vulnerability management and Attack Surface Management (ASM) experts will help create the solution best suited to your needs.
Enjoy maximized security
Enjoy the benefits your new Next-Gen Vulnerability Management solution brings.
See the difference a Next-Gen Vulnerability Management Platform makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.

Since working with Holm Security, the two key components that added value to us are complete visibility and actionable insights. Holm Security has extended coverage with strong reporting. More importantly, they listen to what our organisation needs and adapts improvements to evolving threats. Their experts are quick to support us where we need it most.
Peter Donnelly
Group IT Manager at Keystone GroupLatest news

Outsourcing IT? Then you need Next-Gen Vulnerability Management
Learn why Next-Gen Vulnerability Management is essential for maintaining control, visibility, and compliance in outsourced environments.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.


