Proactively find vulnerabilities across all technical assets
AI-driven threat intelligence finds vulnerabilities across all your technical assets, including business-critical systems/servers, computers, network devices, Operational Technology (OT), Internet of Things (IoT), Kubernetes, cloud-native platforms, and office equipment.
Secure your defenses across technical assets – powered by AI
Asset discovery & monitoring
Integrated Attack Surface Management (ASM) and External Attack Surface Management (EASM) automatically discover assets to find blind spots and shadow IT.
Covers your entire infrastructure
Supports asset discovery and monitoring, as well as finding vulnerabilities in both internet-facing and local networks.
Finds outdated software & misconfigurations
Finds vulnerabilities, outdated software, and much more.
Comprehensive assessment capabilities
Supports multiple assessment capabilities, including authenticated and unauthenticated scanning, Center for Internet Security (CIS) Benchmarks, and local scanners for cloud-native platforms.
Get the hacker's perspective
Determine how secure your organization is if cybercriminals attempt to hack your systems, target you with phishing attacks, or try to spread ransomware.
AI-driven threat intelligence
Our AI-powered Security Research team keeps you updated with the latest vulnerabilities – around the clock, all year round.
Supports the entire workflow
Our Security Center offers a single pane of glass for discovery, prioritization, remediation, and reporting.
Fully automated
Provides automated, continuous asset discovery and monitoring, vulnerability assessments, prioritization, reporting, and follow-up.
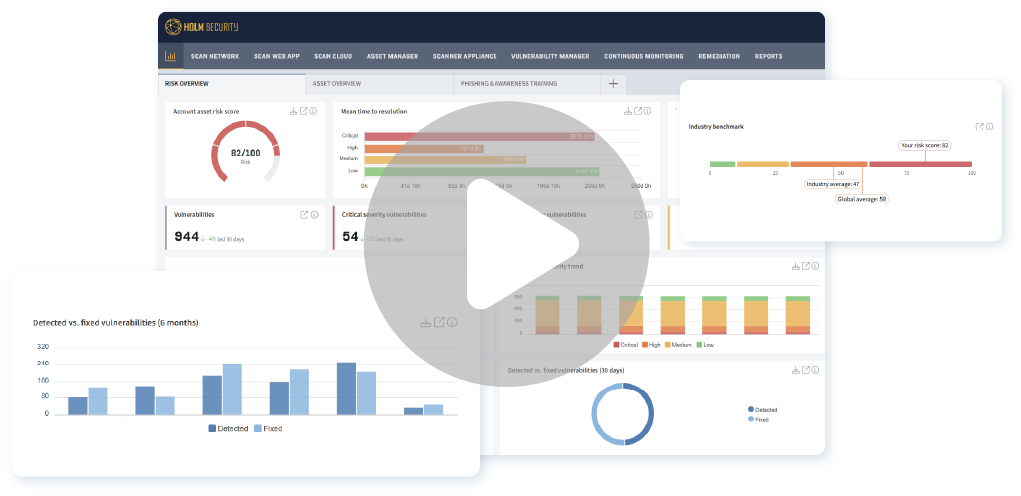
Watch our platform demo
Our market-leading platform is the cornerstone of a proactive cyber defense, empowering you to always stay one step ahead of cybercriminals.
Finding over 200,000 vulnerabilities
Ransomware-related vulnerabilities
Highlights vulnerabilities that are exploited in ransomware attacks.
Outdated systems
Finds vulnerabilities in outdated operating systems, services, applications, and software.
Misconfigurations & weak passwords
Finds all types of misconfigurations, like insufficient permissions, exposed data, and weak passwords in systems, software, and applications.
Blank spots & shadow IT
Continuous and automated asset discovery using Attack Surface Management (ASM) helps you find blank spots and shadow IT.
Get started with a proactive cyber defense today
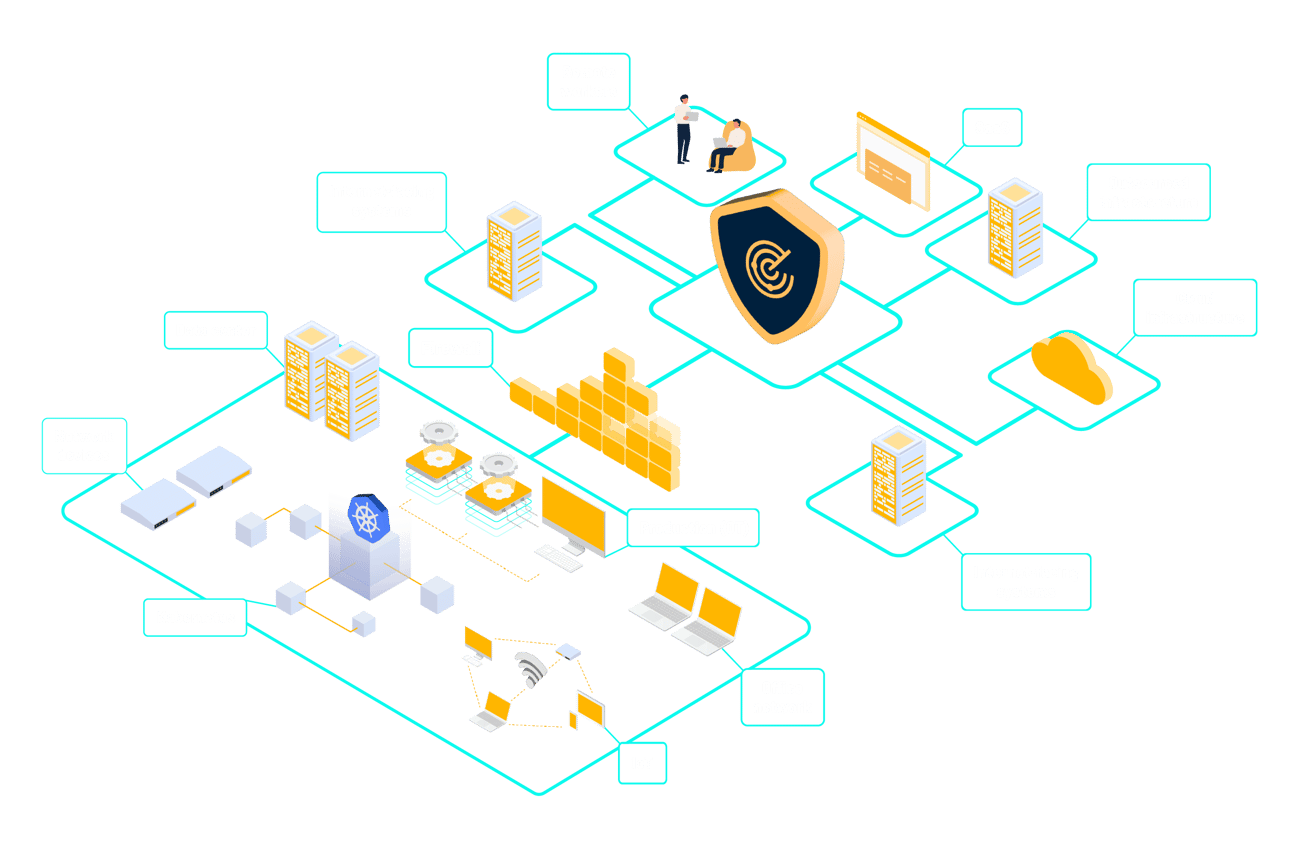
Market-leading attack vector coverage
Systems & servers
OS, software, and services for Microsoft, Linux, Unix, Mac, and other platforms.
Computers
Personal computers inside your office network and remote computers.
Network devices
Network equipment, including routers, switches, and firewalls.
OT
Supervisory layer for Operational Technology systems within production and manufacturing.
IoT
Sensors, diagnostics, monitoring, and alarm systems.
Kubernetes
Cloud and on-prem orchestration platform for containers.
Cloud-native platforms
Cloud-native infrastructure in Azure, AWS, Google Cloud, and Oracle Cloud.
Office equipment
Printers, webcams, and other office devices.
The most powerful platform for compliance
Meet today's & future compliance
New legal requirements, directives, standards, recommendations, and certifications are continuously introduced in response to the growing threat landscape. We help you meet current and future requirements with a systematic, risk-based cyber defense, covering NIS, NIS2, DORA, CRA, GDPR, ISO 27001, and PCI DSS.

Integrated Attack Surface Management (ASM)
Automated from discovery to assessment
Integrating System & Network Security with Attack Surface Management (ASM) and External Attack Surface Management (EASM) fully automates the entire process, from asset discovery and monitoring to finding vulnerabilities.
Benchmark risk against industry peers

Efficiently measure & communicate risk
We provide all the tools you need to measure and communicate risk both internally and externally.
Benchmark your risk
Gain insight into your organization's risk exposure compared to others in your industry.
A complete toolkit with Security Center
Discover
Automatically and continuously discover technical assets with Attack Surface Management (ASM).
Assess
Automatically and continuously assess technical assets.
Prioritize
AI-driven threat intelligence to guide your vulnerability prioritization.
Remediate
Full workflow support for remediation.
Streamline workflows with integrations
SIEM, ticketing, CMDB, CI/CD & more
Integrate vulnerability management into your routine workflow. We offer out-of-the-box integrations with a wide range of systems, including Security Information and Event Management (SIEM), Configuration Management Database (CMDB), patch management, ticketing systems, and Continuous Integration/Continuous Deployment (CI/CD).
Custom integrations
You can create custom integrations tailored to your specific needs using our Application Programming Interface (API).

All features and capabilities in System & Network Security
Cloud-based or on-prem
Get started in hours with minimal maintenance
Our cloud-based deployment option is a comprehensive solution for automated and continuous vulnerability management with no system requirements. It supports organizations of all sizes and environments, regardless of previous experience with vulnerability management. Getting started with our powerful and easy-to-manage platform only takes a few hours.
Best choice for data privacy
We provide the best choice for data privacy and data protection in the industry, with data processing and storage in a neutral country.
Public & local assessments
Our cloud-based platform enables you to scan both internet-facing systems and local infrastructure, providing you with a simple yet powerful solution with comprehensive asset coverage.
Full control over sensitive data, supporting high-security environments
Our on-premise deployment option offers a comprehensive solution for automated and continuous vulnerability management designed to meet the needs of organizations that prefer to keep sensitive data within their own infrastructure. Proxy support allows for secure network communication in high-security environments.
Local deployment - local storage
Installed in your virtual environment, supporting all common virtualization platforms. No sensitive data is communicated over the internet.
Unlimited scanners
Supports unlimited scanners, making it possible to scan your entire infrastructure in one single pane of glass.










.png)
How can we help you?
Your trusted partner

Frequently asked questions
What type of vulnerabilities do you find?
We find a wide range of vulnerabilities, such as outdated systems and software, misconfigurations, weak passwords, exposed personal data, weak encryption, and malware.
Is System & Network Security integrated with Attack Surface Management (ASM)?
Yes, discovered assets will automatically be assessed using the integration.
What is your false-positive rate?
We assess for over 190,000 vulnerabilities with over 99,9% precision.
What type of infrastructure do you assess?
We support assessment of all parts of your infrastructure, including internet-facing and local systems, local and remote computers, network devices, Kubernetes, cloud infrastructure, IoT, and Operational Technology (OT).
Do you support authenticated scanning?
Yes, we support both authenticated and unauthenticated scanning. With authenticated scanning, you can go even deeper to find more vulnerabilities.
Is there any software or hardware required?
It depends on where the asset is deployed.
- Internet-facing scanning using cloud deployment: No software or hardware required.
- Local assessment using cloud or on-premise deployment: A virtual appliance scanner (Scanner Appliance) needs to be installed.
- Assessments with Device Agent: installation of software required.
What is vulnerability scanning?
Vulnerability scanning is the automated process of finding vulnerabilities using a set of network communications with your systems.
How long does it take to get started?
Getting started takes just a few hours. Contact us, and we will help you get started today.
Do you support CIS Benchmark (policy scanning)?
Yes, we support Center of Internet Security (CIS) Benchmarks, or so-called policy scanning. Holm Security is a certified CIS scanning vendor.
What is a scanner?
A scanner is a tool that allows you to assess the security of your systems and networks. It can be used to test for different types of vulnerabilities.
How do you find network vulnerabilities?
We use different technologies to find vulnerabilities, like scanning and agent-based assessments.
What integrations are available?
We provide many out-of-the-box integrations and integration possibilities using our platform API.
