From Reactive to Proactive with Next-Gen Vulnerability Management
In the complex realm of information and communication technology, safeguarding data is just the beginning. Every uncovered vulnerability presents an opportunity for skilled adversaries, ranging from adept hackers to sophisticated state-backed actors. Enhance your cyber security posture and ensure a strong IT environment with our Next-Gen Vulnerability Management Platform.
Addressing Key Cybersecurity Challenges
As ICT infrastructure grows, vulnerabilities and attack vectors also increase. Cyberattacks, including DDoS, ransomware, and phishing, threaten organizations.
Data Breaches
Modern ICT systems are complex and rapidly evolving, making them vulnerable to breaches from software vulnerabilities, human error, and sophisticated cyberattacks. The interconnected nature of technology and factors like legacy systems and economic constraints further exacerbate these vulnerabilities.
Internet of Things
Supply Chain Attacks
Cybercriminals can breach an organization's defenses by conducting supply chain attacks that target suppliers. This strategy can be highly successful since suppliers are typically connected to many organizations and can serve as a backdoor for attackers to infiltrate their intended target's systems.


Get Ready for NIS2
Starting in 2024, the NIS2 directive will require organizations throughout the EU to follow more stringent cybersecurity requirements. By adhering to the directive now, your organization can improve its reputation, gain the trust of customers, and ultimately increase growth and profitability.
-
Unleash the Power of Risk Assessment
Prioritize security gaps and address new risks continuously to stay ahead of cyber threats. Our platform offers incident reporting for incidents and vulnerabilities, allowing you to monitor your security and proactively identify trends. -
Ensure Business Continuity
Our platform enables you to easily identify vulnerabilities, minimize risk, and maintain compliance with just a few clicks. With our help, you can navigate the complexities of NIS compliance with ease, leaving you free to focus on what really matters - growing your business.

GDPR Compliance Made Simple
With Holm Security, you can get a comprehensive assessment of vulnerabilities across your entire attack surface. Our solution can help your security team to efficiently reduce risks. Identify and safeguard systems that store and use sensitive data, preventing GDPR fines.
-
Prioritize Systems Handling Personal Data
Tag specific systems that process personal data as more important than other systems, amplifying the risk score of the asset and ensuring that the vulnerabilities found on these assets are prioritized for remediation. -
Keep Tabs on the Remediation Progress
Integrate with ticketing solutions like JIRA and ServiceNow to seamlessly fold remediation into your IT team’s existing workflow and ensure SLAs are met, and GDPR systems are patched in a timely manner.

Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Empower Your ICT Business with Proactive Cyber Security
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic assets such cloud-based communication systems, remote endpoints, and mobile communication applications that may be dispersed globally and often lie beyond the purview of conventional vulnerability management tools. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
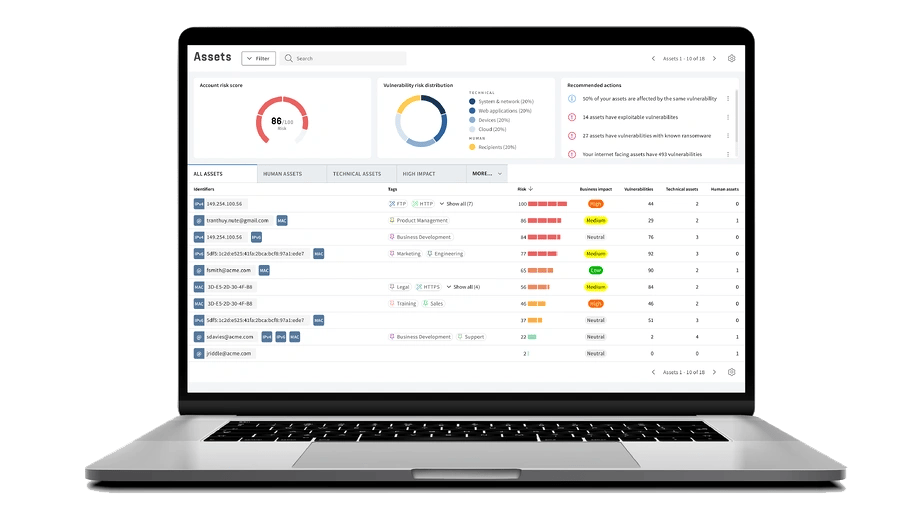
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving the ICT sector and understanding the specific challenges and risks you face. Our solution is designed to tackle the vulnerabilities inherent in your industry.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your internal processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest news

5 ways to create a successful vulnerability management program
A successful vulnerability management program requires these 5 key components.

Coming up in 2025: Building the future of Next-Gen Vulnerability Management
Whether you manage thousands of endpoints or complex cloud infrastructure, our platform is evolving to meet your needs - with greater precision and flexibility than ever before.



