Securing containerized environments with Kubernetes security

Kubernetes has revolutionized how organizations build, deploy, and scale applications. It is scalable, dynamic, and widely adopted across public clouds, private clouds, and on-premise data centers. However, as Kubernetes environments become increasingly complex, they also become more attractive targets for attackers. Its flexibility introduces new risks: misconfigurations, privilege escalation, and exploitation opportunities that can compromise entire clusters if left unchecked.
That’s why we’re excited to announce a major step forward in helping organizations protect their containerized environments: Kubernetes security, now available in our System & Network Security product.
Kubernetes: Widely used, difficult to secure
Kubernetes has become a cornerstone of production workloads for many organizations embracing cloud-native environments. In fact, a 2023 Cloud Native Computing Foundation survey found that 89% of respondents were using, or planning to use, Kubernetes. Moreover, more than 90% of organizations where much, or nearly all, of their app development and deployment is cloud native rely on containers. Yet, securing Kubernetes remains difficult.
Misconfigurations - like overly permissive roles, open network policies, or exposed services - can turn an otherwise well-architected cluster into an easy entry point for attackers. Recent high-profile breaches, like last year’s exploit of critical vulnerabilities in OpenMetadata to gain unauthorized access to Kubernetes workloads and leverage them for cryptocurrency mining, have shown that containers are no longer invisible to cybercriminals. Once inside, attackers can pivot across environments, exploiting blind spots that traditional network or vulnerability management tools simply don’t see.
We now equip our customers with the tools they need to address these problems.
 A unified view of Kubernetes environments
A unified view of Kubernetes environments
Our new Kubernetes security capability extends powerful visibility into your containerized infrastructure.
With it, you can now:
- Discover Kubernetes clusters across both cloud and on-prem environments automatically.
- Authenticate to the Kubernetes API for deep inspection of configurations and workloads.
- Scan for misconfigurations with over 250 targeted checks, detecting issues like insecure roles, risky network policies, and exposed services.
- Assess discovered services for vulnerabilities, integrating containerized environments into your end-to-end vulnerability workflows.
In other words, Kubernetes is now part of the same connected map of assets, risks, and remediation workflows that customers already manage through our platform.
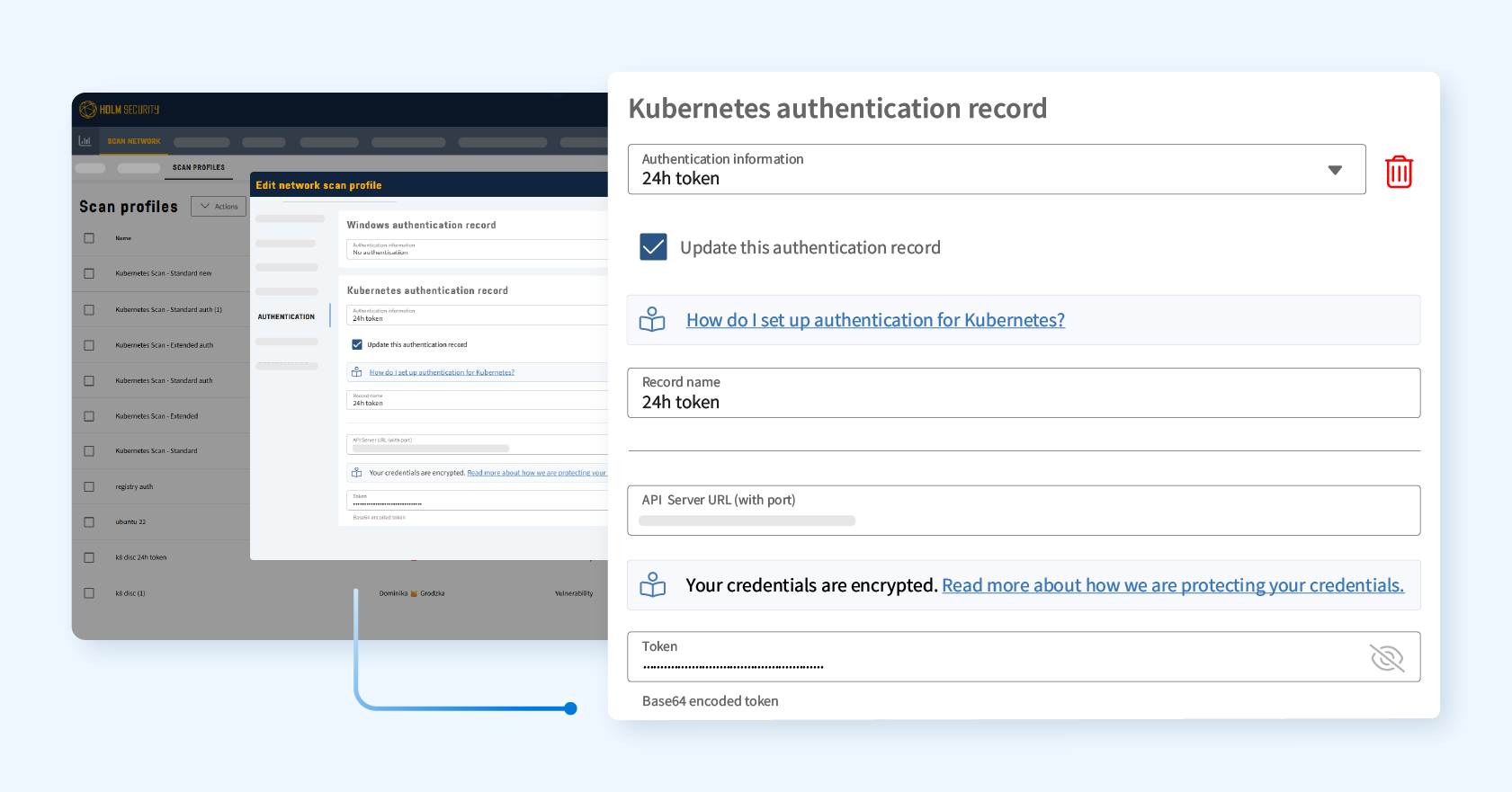 Seamless, scalable, and easy to use
Seamless, scalable, and easy to use
We designed Kubernetes security to work seamlessly with existing deployments. Once authentication records are in place, every network scan can automatically detect Kubernetes clusters for greater attack surface visibility. For internal or restricted environments, simply deploy a Scanner Appliance, and we’ll securely perform assessments from within your network perimeter.
The result? A more accurate and complete understanding of your security posture - without added operational overhead. By bringing containers into your broader security ecosystem, you can finally see - and secure - your entire environment with confidence.
With Kubernetes security, we’re closing the gap between traditional and cloud-native infrastructure, giving security teams a unified view to detect, prioritize, and remediate risks wherever they emerge.
Get started with Kubernetes security
Ready to secure your Kubernetes clusters? Keep them out of the hands of criminals by reaching out to our Sales team today.

Anna Wagner
Content Marketing Manager
With nearly a decade of international experience, Anna's strength lies in bridging the gap between the creative and the technical with strategy in mind. With previous experience in tech scale-ups and cyber security, such as at Wealth-X and BlueVoyant, Anna breaks down what you need to know so you spend less time reading between the lines.




