Safeguarding the Seas with Next-Gen Vulnerability Management
Empower your shipping and maritime business with comprehensive vulnerability assessments for every offshore and onshore site. No matter the hardware, location, scale, or connectivity, we provide a thorough snapshot of your network assets and potential threats. With our proactive Next-Gen Vulnerability Management Platform, we'll help you pinpoint existing vulnerabilities but also equip you to address future challenges.
Addressing Key Cybersecurity Challenges
Phishing
The human element remains one of the most significant vulnerabilities. Phishing attacks can target crew members or port staff to gain unauthorized access to systems or sensitive information. All personnel, including ship crews and port operators, need ongoing cyber threat training to learn how to prevent attacks.
Operational Technology
An attack on OT systems can result in physical damages, like interference with ship navigation systems (leading to collisions or groundings), disruption in port operations, or even sabotage of equipment. Many OT systems in the maritime sector were not designed with cyber security in mind and can be outdated, making them more susceptible to threats.
Supply Chain
The maritime industry is deeply intertwined with complex supply chains. An attack on one entity can have cascading effects on others. Vendors or third-party service providers with inadequate cyber security measures can introduce vulnerabilities, making the entire supply chain vulnerable.



Get Ready for NIS2
In 2024, NIS2 will set a new cybersecurity benchmark for sectors across the EU. We'll help you enhance your standing, secure customer trust, and ensure compliance.
-
Unleash the Power of Risk Assessment
Prioritize security gaps and address new risks continuously to stay ahead of cyber threats. Our platform offers incident reporting for incidents and vulnerabilities, allowing you to monitor your security and proactively identify trends.
-
Ensure Business Continuity
Our platform enables you to easily identify vulnerabilities, minimize risk, and maintain compliance with just a few clicks. With our help, you can navigate the complexities of NIS compliance with ease, leaving you free to focus on what really matters - growing your business.
International Maritime Organization
IMO (the International Maritime Organization) is the United Nations' specialized agency with responsibility for the safety and security of shipping. IMO provides guidelines and recommendations for maritime cyber risk. Stakeholders should take the necessary steps to safeguard shipping from current and emerging threats and vulnerabilities related to digitization, integration, and automation of processes and systems in shipping. IMO’s recommendations clearly state that identifying vulnerabilities and risks is required within the maritime industry.
Internal Chamber of Shipping
ICS (Internal Chamber of Shipping) is the global trade association for shipowners and operators. ICS has specific guidelines for cyber security onboard ships produced and supported by BIMCO, CLIA, ICS, Intercargo, Intermanager, Intertanko, IUMI, OCIMF, and the World Shipping Council. These guidelines focus on the need for cyber risk management, the importance of identifying vulnerabilities, and the need for risk-based work.
Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Protect Your Ship & Crew
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. Ensure the safety, security, and protection of the ship, crew, cargo, and marine environment. Our platform can help maintain the smooth and timely operation of your business. -
Scan Infrastructure Onboard
Connectivity challenges at sea restrict the speed and timing of data communication to centralized systems for cyber security. Holm Security's vulnerability management platform minimizes the amount of data to be transmitted whenever possible. Thus, the vulnerability data from onboard systems can be efficiently managed centrally directly in the cloud.
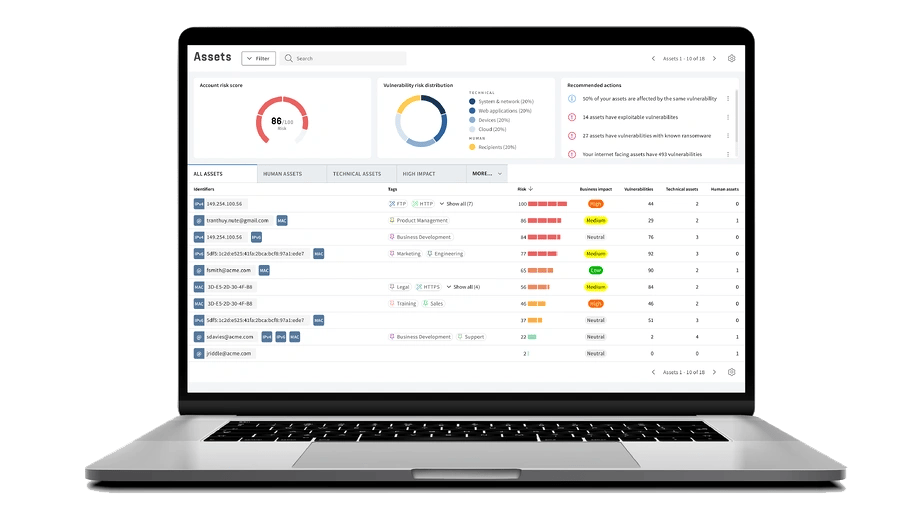
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving the maritime sector and understand the specific challenges and risks you face. Our solution is designed to tackle the vulnerabilities inherent in your industry.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your existing processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest News

DORA Decoded: Fusing Operational Resilience & Vulnerability Management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade Your Cyber Defense To Comply With NIS2 - A Step-by-Step Guide On How To Prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cybersecurity posture and adhere with NIS2 regulations.




