Secure, Defend & Protect with Next-Gen Vulnerability Management
Municipalities face the dual challenge of safeguarding citizens' data while delivering flexible, high-quality services. Tasked with managing numerous systems and adhering to local laws and regulations like GDPR and NIS, they often find themselves at the crossroads of increasing cyber security demands. With heightened susceptibility to cyberattacks, reinforcing cyber security becomes paramount. Let us guide you in identifying and addressing your vulnerabilities, both now and in the future, with Next-Gen Vulnerability Management.
Navigating Cyber Security Challenges
Legacy Systems & Infrastructure
Many municipalities still rely on outdated IT infrastructure and legacy systems that may not have been designed with modern cybersecurity threats in mind. Updating these systems can be expensive and complex, but failing to do so makes them vulnerable to attacks.
Limited Resources
Unlike large corporations, many municipalities operate with limited budgets and might not have the funds to hire a full-fledged cybersecurity team or invest in advanced security solutions. This lack of resources can leave you exposed to threats that larger entities might be better equipped to handle.
Phishing
Municipalities handle a wealth of sensitive data ranging from citizens' personal details to property tax records and even utility billing. Be cautious and stay informed because a successful phishing attack can grant cybercriminals access to all this information, putting them at risk of identity theft, fraud, or other misuse.


Prepare for NIS2 & Elevate Cyber Security
With the onset of the NIS2 directive in 2024, municipalities across the EU are set to encounter more rigorous cybersecurity standards. Early compliance can not only elevate public trust but also streamline operations.
-
Safeguard Public Services
Through our platform, effortlessly pinpoint vulnerabilities, diminish risks, and uphold NIS2 compliance. By alleviating the intricacies of cybersecurity compliance, municipalities can invest more time and resources in enhancing community services and development.
-
Ensure Business Continuity
Stay a step ahead of potential cyber threats. Our platform provides continuous security gap prioritization and features incident and vulnerability reporting. This enables your municipality to proactively monitor your security landscapes and discern patterns.

Achieve GDPR Compliance with Ease
Municipalities handle immense volumes of personal data daily. With GDPR's stringent requirements, it's paramount to secure all systems managing or processing this data. Non-compliance not only results in hefty fines but could also jeopardize citizen trust. Holm Security offers a streamlined approach:
-
Targeted Protection of Sensitive Systems
With Holm Security, prioritizing systems processing personal data is easy. By enhancing the risk score of these critical assets, we ensure that their vulnerabilities receive immediate attention for remediation.
-
Keep Tabs on the Remediation Progress
Seamlessly integrate with platforms like JIRA and ServiceNow to blend remediation tasks into your IT workflows. This ensures SLAs are honored and GDPR-related systems are addressed promptly.

Start Your NIS2 Compliance Journey
Try Our Platform for Free Today!
Empower Your Security Team
& Maximize Efforts
Through years of collaboration with municipalities, we have gained much experience in the public sector. This experience is reflected in our Next-Gen Vulnerability Management Platform. We have spent much time optimizing our platform to best suit the needs of your municipality. We aim to provide continuous insight to ensure that your organization, IT environments, and citizens are well protected.
-
Comprehensive View of Your Digital Infrastructure
Achieve a crystal-clear understanding of all digital assets and associated vulnerabilities. This extends beyond just your main servers, reaching into areas such as cloud services, remote workstations, municipal mobile applications, or other areas that frequently elude traditional vulnerability management tools. With our platform, you can ensure no asset is overlooked, allowing for prioritized, effective mitigation efforts.
-
Elevate Your Municipality's Cyber Defense Strategy
Avoid allocating resources to vulnerabilities that aren't of immediate concern. Our Unified Vulnerabilities dashboard gives you a panoramic view of all potential risks – from network vulnerabilities to phishing attempts targeting your staff. With our innovative threat score system, vulnerabilities are ranked not just by technical severity, but also by their potential impact on human and physical assets, ensuring that your risk management strategy is both efficient and effective.
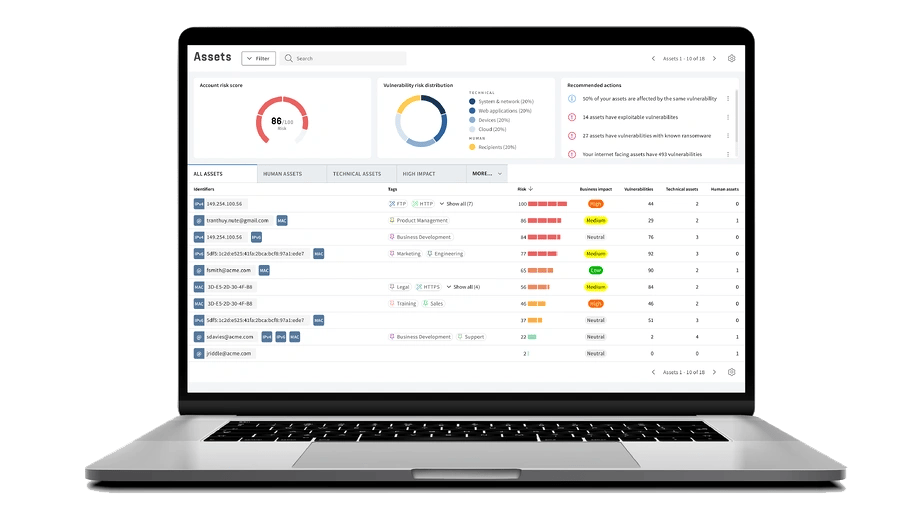
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving municipalities understanding the specific challenges and risks you face. Our solution is designed to tackle the vulnerabilities inherent in your industry.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your production processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest News

DORA Decoded: Fusing Operational Resilience & Vulnerability Management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade Your Cyber Defense To Comply With NIS2 - A Step-by-Step Guide On How To Prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cybersecurity posture and adhere with NIS2 regulations.




