Transforming Classrooms with Next-Gen Vulnerability Management
The education sector has consistently grappled with hurdles like limited IT budgets and resources. As cyberattacks targeting educational institutions intensify daily, inadequate cyber security measures jeopardize student data. A structured, systematic, and proactive cyber security defense strategy is necessary to stay safe and protect against financial loss, prevent disruption, and protect students from harm. We’ll help you understand and remediate the vulnerabilities you have - today and tomorrow.
Keeping Your Students Safe
Widespread Disruption
Distributed denial-of-service (DDoS) attacks are a common type of attack on all educational institutions. They're often performed to cause widespread disruption to the network, negatively impacting productivity. It's a relatively easy attack for an amateur cyber-criminal, especially if the target network is poorly protected.
Sensitive Information
Ransomware Attacks
Another motive for hackers attacking educational institutions is financial gain through ransomware attacks, especially for universities handling hefty student fees. Without proper protection, this presents a weak spot for cybercriminals to intercept.
Data You Can Act On
Discover how Whitgift School utilizes our platform to keep its students and staff secure, leverage their security with actionable data, and prevent future attacks.

See For Yourself
Try Our Platform for Free Today!
GDPR Compliance Made Easy
Educational institutions like schools and universities handle vast amounts of student data. With GDPR emphasizing the security of systems processing personal data, leaks can lead to hefty fines and potential harm to students. To address this critical need:
-
Focus on Crucial Assets
Holm Security empowers institutions to highlight systems processing personal data, intensifying their risk score. Ensure vulnerabilities on these crucial assets are addressed foremost, safeguarding sensitive data and evading GDPR penalties.
-
Efficient Remediation Workflow
Seamlessly integrate with platforms like JIRA and ServiceNow. Monitor remediation progress, guarantee adherence to SLAs, and promptly patch GDPR-critical systems.

Empower Your Security Team
& Maximize Efforts
Holm Security delivers the broadest coverage and most thorough assessment of vulnerabilities across your entire attack surface. By leveraging our solution, your security resources can make a greater impact on risk reduction with minimal effort.
-
See Your Entire Attack Surface
Gain precise comprehension of all assets and vulnerabilities across your entire attack surface. This includes dynamic elements like cloud-based learning platforms, remote learning devices, and educational mobile apps, which may be distributed across various locations and sometimes extend beyond the reach of conventional security tools. With increased visibility, you can prioritize mitigation efforts and guarantee comprehensive protection. -
Transform Your Organization's Cyber Defense
Don't waste your time on vulnerabilities that don't pose a real threat. Our Unified Vulnerabilities view lets you track all risks in one place, including network, web, device, and phishing recipients. The new threat score prioritizes vulnerabilities for technical and human assets, making risk management easier.
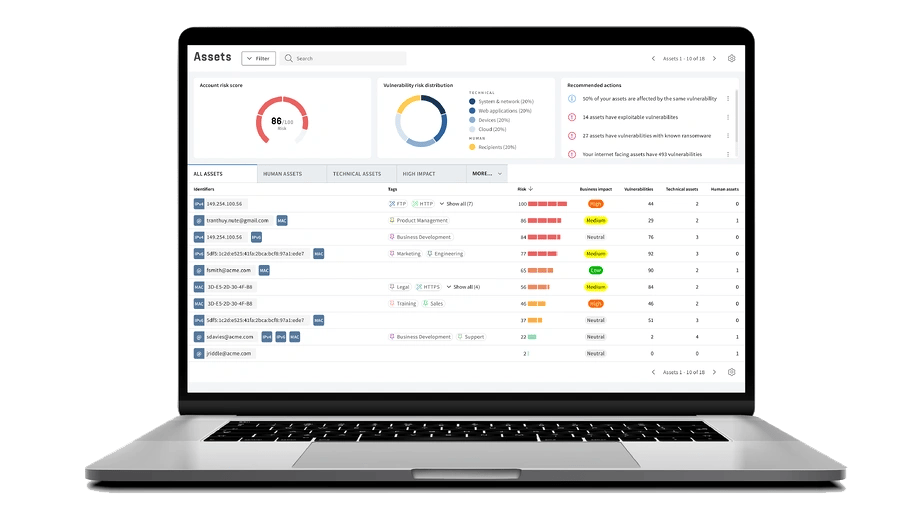
Get A Complete Picture of Your Cyber Security Defense
Detect
Scan every potential entry point for attackers. Efficiently monitor and manage all of your systems, applications, endpoints, and employees.
Assess
Up your security game with fast and accurate scans, and prioritize the vulnerabilities that truly put you at risk from the ones that don’t.
Remediate
Cut down on unnecessary headaches with straightforward risk in real-time right from your dashboard. Measure and communicate progress effectively.
See For Yourself
Try Our Platform for Free Today!
Why Choose Our Vulnerability Management Solution?
Industry Expertise
We specialize in serving the education sector, understanding the specific challenges such as student data protection and online learning security that you face. Our solution is tailored to address the vulnerabilities inherent in your field, ensuring a safe and productive educational environment.
Minimal Disruption with Maximum Protection
Our solution is implemented seamlessly into your existing infrastructure, providing robust protection without interrupting your production processes.
Comprehensive Threat Detection
Our comprehensive platform provides exceptional visibility and insight, encompassing all assets, technical and human. Maximize your efforts and reduce business-critical risks with the least amount of effort.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.
Latest News

DORA Decoded: Fusing Operational Resilience & Vulnerability Management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade Your Cyber Defense To Comply With NIS2 - A Step-by-Step Guide On How To Prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cybersecurity posture and adhere with NIS2 regulations.





