Covering all attack vectors.
Get Secure with Next-Gen Vulnerability Management.
Mitigate business risks and fortify your digital stronghold with Holm Security. Our cutting-edge platform ensures a resilient and future-ready security posture for your business, empowering you to always stay one step ahead of cybercriminals.
Next-Gen Vulnerability Management vs. Traditional
Efficient, Smarter & More Complete in the Fight Against Evolving Cyber Threats
Our next-gen platform is more than just a holistic approach to cyber security. Our platform, which includes the 4 pillars that you see here on the right, is designed to keep you ahead of potential cybercriminals by continuously monitoring vulnerabilities and providing real-time threat intelligence. Combine these with our customized employee training programs, and you have a robust, integrated security protocol that covers all of your assets and empowers your employees to be vigilant and proactive.
Our Next-Gen Vulnerability Management Platform provides a 360-degree security framework to withstand both current and future cyber threats.
Unparalleled Attack Vector Coverage
Create a tightly woven security net that not even the most advanced threats can slip through. Monitor your IT infrastructure at every conceivable point of attack to ensure your data, assets, and reputation remain secure.
Attack Surface Management
Identify and address emerging vulnerabilities and adjust your protective measures accordingly, ensuring that your attack surface remains minimal and fully secured.
Smart Threat Intelligence
Our threat intelligence services use advanced analytics, machine learning algorithms, and industry-specific expertise to provide a tailored view of the threat landscape for your organization.
True Unification
Consolidate all threat data and risk factors into a single, easy-to-use interface for optimal oversight and action. Gone are the days of multiple platforms and dashboards to understand your security posture.
The Modern Attack Surface Has Outgrown Traditional Vulnerability Management
Incorporating modern technologies in day-to-day operations presents a broader range of attack vectors for potential exploitation. The attack surface has expanded, making traditional vulnerability management methods insufficient in dealing with these sophisticated attacks. The scope of vulnerability management needs to extend beyond just systems and web applications to include other critical components such as network infrastructure, cloud services, mobile devices, and even IoT (Internet of Things) devices.
Limited Attack Vector Coverage
Scanning only your systems and web apps may leave blind spots and hidden vulnerabilities in your infrastructure, leaving a considerable attack surface unprotected.
Out of Context Risks
Not all vulnerabilities are created equal. Traditional vulnerability management doesn't take into account how each vulnerability relates to the unique aspects of your organization’s operations, assets, or threat landscape.
Too Many Tools
Over time, many organizations have built up a significant product stack, relying on multiple tools and products that are not integrated - costly and often require additional effort to interpret the findings.
No User Awareness
Users are the first line of defense, but a traditional vulnerability management program does not address this.
Next-Gen Vulnerability Management Platform
Continuously Monitor.
Identify Vulnerabilities.
Remediate Misconfigurations
Gain complete visibility and actionable context on your most critical misconfigurations, so your teams can proactively and continuously improve your cloud security posture. Enjoy the core capabilities of CSPM, vulnerability management – in a single solution.
Manage Complex
Vulnerabilities with
Clarity & Ease
Take control of your cyber security with System & Network Scanning. We cover all parts of your infrastructure – public and local systems, local and remote computers, network devices and equipment, cloud infrastructure, IoT, and OT/SCADA.

Efficiently Minimize Risk in Modern Web Applications
Reduce your attack surface and identify a wide range of vulnerabilities within your websites and web apps – including cross-site scripting (XSS), SQL injection, and OWASP Top 10 vulnerabilities. Also supports scanning of your APIs to keep them secure.

Change Behavior.
Reduce Risk.
Create Resilience
Don't let human error be your organization's weakest link in cyber security. Enhance your human firewall using realistic email simulation exercises, including phishing, spear phishing, executive impersonation fraud, and ransomware threats. Bolster employee resilience through customized, automated, and targeted awareness training.

Full Visibility.
Complete Security.
Scan It All
Elevate your API security effortlessly. Identify and resolve vulnerabilities, ensuring no potential entry points are left unscanned or exposed to attacks. Safeguard your externally facing applications confidently.
The Number of Vulnerabilities We Detect
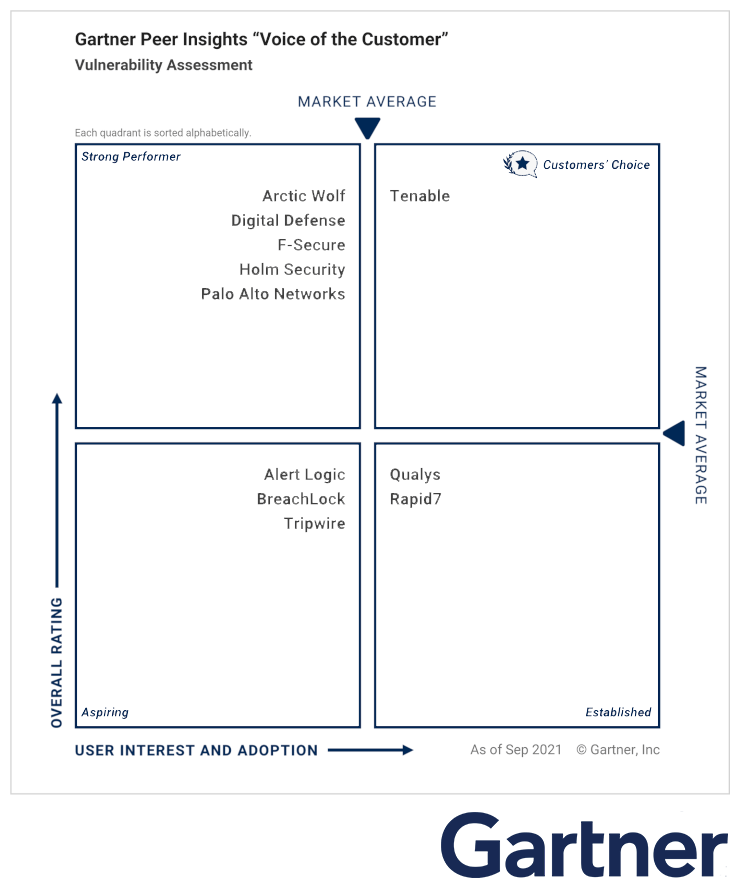
Gartner: Voice of the Customer
Holm Security is pleased to announce our inclusion in Gartner's "Voice of the Customer" report. This report is based on reviews from Gartner Peer Insights, which recognizes vendors and products highly rated by their customers. Our success is attributed to our ability to effectively address our customers' needs. To fully understand the extent of our achievements, we encourage you to read the individual reviews and ratings shared by our satisfied customers on Gartner Peer Insights.
See for Yourself
Try Holm Security VMP for Free
Start your free trial today.
Your Tailored Vulnerability Management
Solution is 3 Steps Away
Book a
Meeting
During the initial call, our team will get and understanding of your business technology status and needs.
Get Your Custom Solution
Our vulnerability management experts will help create the solution best suited to your needs.
Enjoy Maximized Security
Enjoy the benefits your new Next-Gen Vulnerability Management solution brings.
See the Difference a Next-Gen Vulnerability Management Platform Makes
From local government to industry-leading retailers, discover how Holm Security helps solve cyber security problems.

Since working with Holm Security, the two key components that added value to us are complete visibility and actionable insights. Holm Security has extended coverage with strong reporting. More importantly, they listen to what our organisation needs and adapts improvements to evolving threats. Their experts are quick to support us where we need it most.
Peter Donnelly
Group IT Manager at Keystone GroupABOUT US
Empowering Companies Struggling to Gain Insight into Their Cyber Security Posture
Latest News

DORA Decoded: Fusing Operational Resilience & Vulnerability Management
In this blog post, we're diving deep into DORA - why it's vital for digital service providers and financial institutions and why you should care about it.

Upgrade Your Cyber Defense To Comply With NIS2 - A Step-by-Step Guide On How To Prepare
This webinar will focus on the practical steps that IT departments need to take to improve their cybersecurity posture and adhere with NIS2 regulations.


